Resources
Top Four Protections on Cloud Apps from Unmanaged Devices
By Suhaas Kodagali - Product Management Lead
June 14, 2023 5 Minute Read

In a post-covid, remote working world, enterprise security teams are looking to expand protections across many security vectors. One of them that is receiving a lot of focus is devices – the ability to apply controls based on the device type that is accessing corporate data resources. The dominant share of devices accessing company data is managed devices, which mostly includes employees using computers or phones that are provided and controlled by the organization. Managed devices adhere to the organization’s policies and standards, allow for centralized management, security controls, and software updates, thereby ensuring a higher level of control and security. But in the recent decade, the share of traffic coming from unmanaged devices is growing steadily, raising security concerns.
Recent research indicates that bring your own device (BYOD) still remains the norm, with a significant number of companies allowing the use of personal (or unmanaged) devices in the workplace. Unmanaged devices include personally owned devices used by employees, as well as devices from third-party suppliers, vendors, partners, and other external entities. These unmanaged devices operate outside the organization’s direct control and can introduce potential security vulnerabilities and risks to the network and data. Despite security concerns, enterprises allow them because they add business value. They help employees remain productive when managed devices may not be accessible, as when on vacation. They also facilitate collaboration with partners, suppliers, and contractors, who are critical to the running of many organizations.
Enterprise security teams are coming to terms with the fact that unmanaged devices accessing corporate cloud apps is a phenomenon that is here to stay. Given this, their primary concern is one of data protection within sanctioned SaaS apps such as OneDrive, Salesforce, Google Workspace, Slack or ServiceNow. For instance, if a contract employee is accessing corporate documents on OneDrive from an unmanaged device, then I want to ensure that they don’t download any internal roadmap or planning documents. Or, I want to ensure that an employee on the Sales team who is moving to another company does not download sales report data or customer contacts from Salesforce. To address these concerns, security teams use their Security Services Edge (SSE) solution to define and enforce these controls. The most important controls that customers apply on traffic from unmanaged device are –
- Visibility and data protection into unmanaged devices accessing sanctioned SaaS apps:
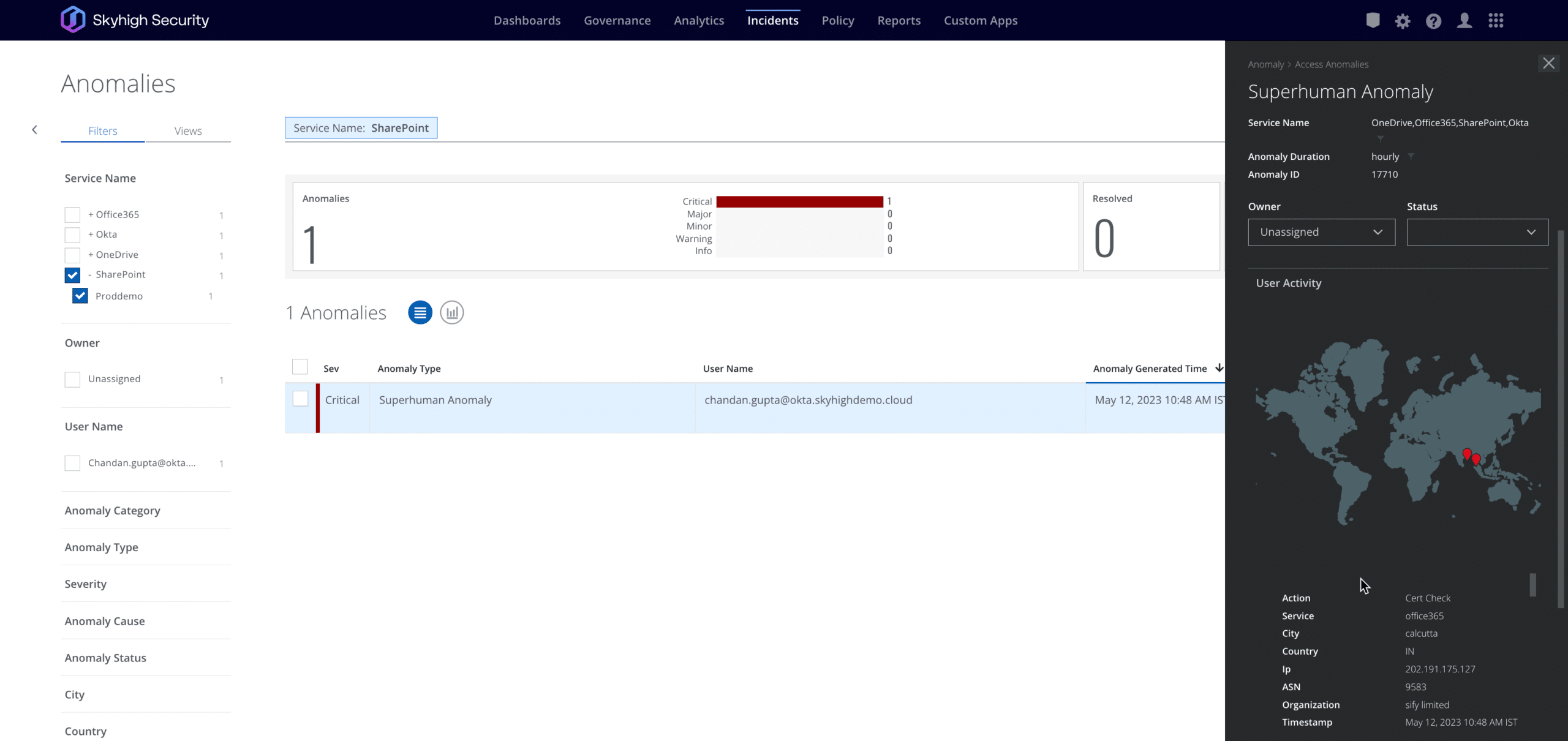
When employees or third-party users access companies’ corporate apps via unmanaged devices, security teams want to ensure they have visibility into the activity performed and a record that the organizations’ controls were applied on this access. For example, detection of anomalous usage should not be hampered just because an employee who didn’t have access to her laptop decided to use her personal iPad to update a presentation on SharePoint. Customers using the Skyhigh Security SSE solution have comprehensive visibility into all activity coming from unmanaged devices into corporate apps by virtue of an API integration, which is device agnostic. So, customers can apply comprehensive controls which include data loss prevention (DLP), forensic analysis (through visibility into activities), detecting threats, identifying misconfigurations, and controlling third party connected apps. By offering the most expansive API integrations list in the SSE market, Skyhigh Security enables its customers to apply these security controls to a broad range of sanctioned Software-as-a-Service (SaaS) applications.
- Block exfiltration of corporate data from sanctioned SaaS apps onto unmanaged devices:
The biggest concern that security teams have with unmanaged devices accessing company sanctioned cloud apps is that they can download data into the device, after which the company loses all control on what they do with the data. To prevent this, they want to apply controls to prevent download of any files if the access is from an unmanaged device. So, the user is able to view and edit a file but cannot download it. But, exfiltration of data doesn’t always happen with download; a user can extract data through other means, such as copy-paste or printing. So, these actions need to be controlled as well. Skyhigh Security customers have a unique solution to address this problem. Using a combination of its Cloud Access Security Broker (CASB) and Remote Browser Isolation (RBI) technologies, Skyhigh Security is able to redirect traffic from an unmanaged device into an RBI session and enforce granular controls to block actions such as upload, download, copy, and print which can exfiltrate sensitive data.
- Prevent exfiltration of sensitive data from private apps:
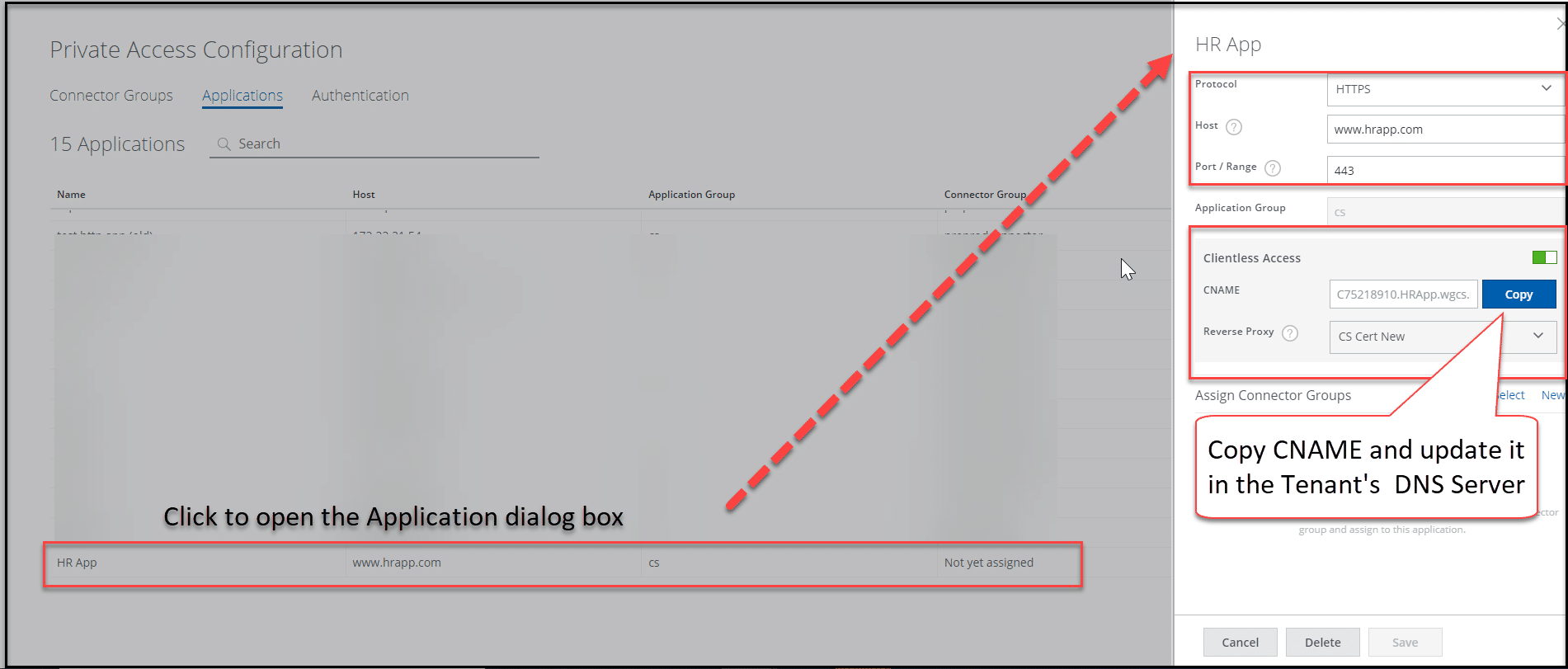
Homegrown or private apps are increasingly becoming the focus of enterprise security controls as enterprises are looking to enforce Zero Trust access controls to only allow those users who need access to these apps. In many cases, companies require third party users to access these apps as well, as they include procurement, payroll, or development-based apps. This requires them to allow access via unmanaged devices, and consequently apply the necessary protections as well. Skyhigh Security customers use Skyhigh Private Access to apply secure controls including access controls and DLP. For unmanaged devices, customers can use the Clientless Access option that empowers end users to authenticate and establish a secure connection to private applications using only a web browser. Security teams also have the option to redirect traffic from unmanaged devices through an RBI session just like with SaaS apps. With the Clientless Private Access option, the process of installing and managing additional software is eliminated, streamlining access to critical resources. This tremendously helps to provide access and control to private applications to users on unmanaged devices.
- Prevent upload of malware into corporate SaaS apps:
Unmanaged devices don’t usually have the necessary security controls and have users downloading data from any number of social media and unregulated apps. When these devices are used to upload files into a company’s sanctioned SaaS apps, then a malware infection could spread to the cloud instance and potentially spread to sync’d devices. By pushing traffic from unmanaged devices into an RBI session, Skyhigh Security customers are able to perform comprehensive malware checks on this data to filter out any potentially harmful file.
The business need to allow access from unmanaged devices is clear, but the security threat from unmanaged devices is real. Recent research shows that a majority of employees engage in risky behavior on personal mobile devices – 71% store sensitive work passwords on their phone and 66% use personal messaging apps for work purposes. So, enterprises have to secure against this threat vector by applying the necessary controls. To do this, they are relying on leading SSE solutions like Skyhigh Security so they can allow employees and partners to access corporate cloud apps without compromising security and compliance requirements.
To learn more about what Skyhigh Security products can do for you, request a demo today.
Back to BlogsRelated Content
Trending Blogs
LLM Attributes Every CISO Should Track Today
Sarang Warudkar February 18, 2026
From DPDPA Requirements to Data Visibility: The DSPM Imperative
Niharika Ray and Sarang Warudkar February 12, 2026
Skyhigh Security Q4 2025: Sharper control, clearer visibility, and faster action across data, web, and cloud
Thyaga Vasudevan January 21, 2026
The Hidden GenAI Risk That Could Cost Your Company Millions (And How to Fix It Today)
Jesse Grindeland December 18, 2025
Skyhigh Security Predictions: 2026 Is the Year AI Forces a New Blueprint for Enterprise Security
Thyaga Vasudevan December 12, 2025