Skyhigh Security Solutions
Identify & Protect Sensitive Data
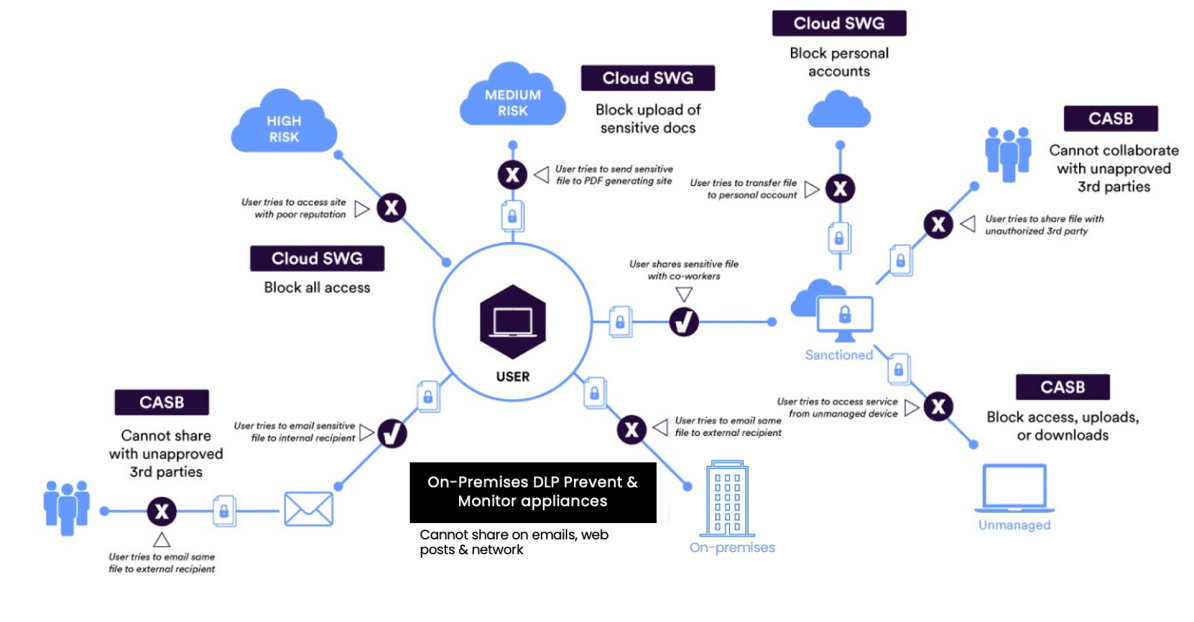
Skyhigh Security’s unified approach to data protection provides complete visibility and control from device to cloud. Eliminate visibility gaps, providing full scope protection for your workforce. Unify data protection for data across endpoints, web, private apps, email and cloud. Enable unified reporting and incident management without increasing overhead.

Understand how your corporate data is being used, including data at rest, data in use and in motion. A single DLP solution that leverages one engine and a set of classifications across endpoint, web, cloud, email and private apps.
Manage all DLP violations and reporting via a single dashboard, with integrated incident workflow and detailed evidence information about incidents.
Ensure compliance with different regulations, using many out of the box compliance templates.
Improve user awareness with end user notifications and self-service incident remediations.
Leverage advanced DLP technology, like classifications, IDM, EDM, and OCR, to efficiently identify data important to your business, reducing false positives and exfiltration risks.
Achieve broad visibility with continuous or on-demand scanning of data at rest in the cloud and granular control of data movement.
Resources