Skyhigh Data Security Posture Management (DSPM)
Elevate Your Data Security with an SSE enabled DSPM solution
A unified solution for managing and securing your organization's data assets, simplifying operations, and delivering faster value.

The Data Security Challenges of Modern Enterprises
Modern enterprises operate in dynamic, complex environments, facing unique security challenges to protect the most valuable asset – their data.
Lack of visibility into where sensitive data resides and how it is being used across hybrid or multi-cloud environments, as well as within shadow IT systems and GenAI services.
The lack of comprehensive data risk remediation makes it challenging for organizations to address and secure sensitive data vulnerabilities, misconfigurations, and improper data handling across cloud environments.
The need for innovation, through multi-cloud, AI services, and new ways to collaborate, is fueling a data explosion that expands the attack surface and makes security and compliance harder to manage.
Fragmented security tools, which require multiple solutions to monitor and protect data across diverse cloud environments, result in inefficiencies and increased costs.
Rising enterprise data risks, including shadow data, misconfigurations, insider threats and new compliance regulations.
Enterprises struggle to maintain compliance frameworks (e.g., GDPR, HIPAA, CCPA) and provide sufficient auditing information due to inadequate reporting and monitoring tools.

Omdia Rates Skyhigh Security DSPM 'Best in Class' for Advanced Capabilities
The Omdia Universe: Data Security Posture Management (DSPM), 2025 report is officially live, and Skyhigh Security DSPM earned top recognition across multiple categories. We are proud to share that our solution was named Best in Class for advanced capabilities, while also being rated top-tier for core capabilities, solution breadth, and vendor execution. This recognition underscores our leadership in delivering comprehensive, advanced DSPM solutions for modern enterprises.
Solving Modern Data Protection Challenges with DSPM
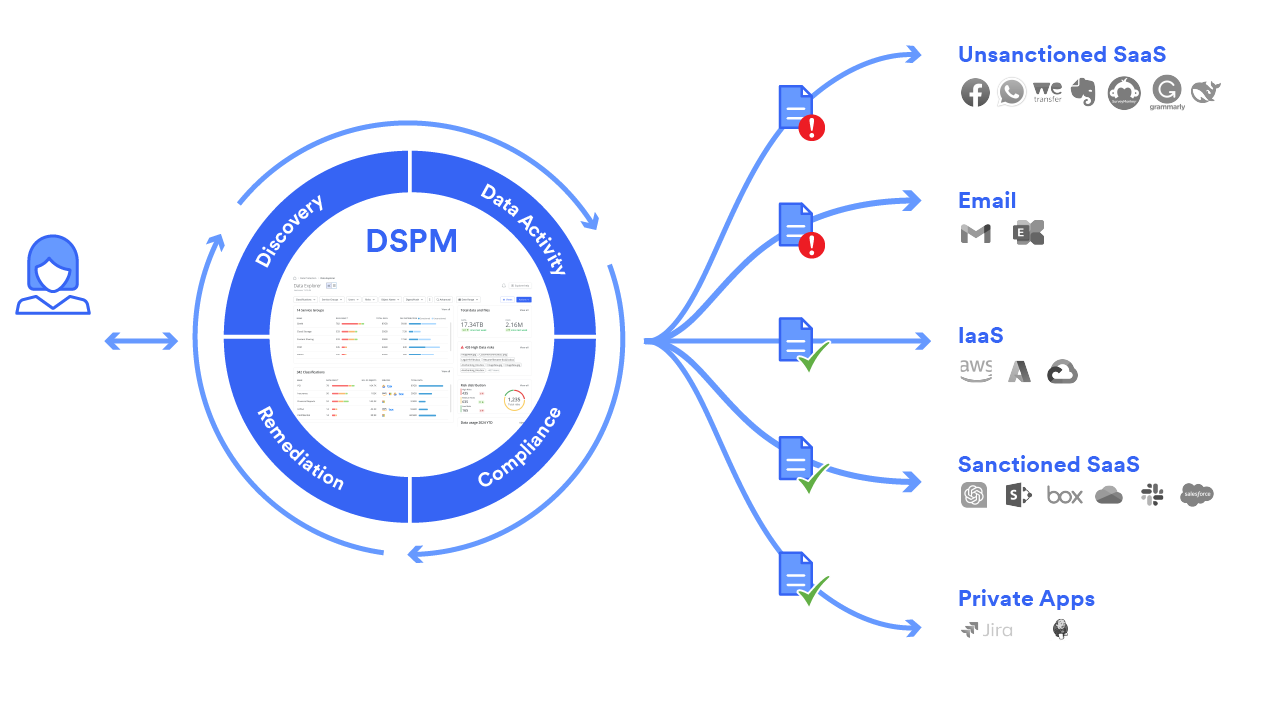
Organizations are embracing multi-cloud, AI services, and collaboration tools to drive innovation, but the resulting data explosion expands attack surfaces, complicates security and compliance.
Learn MoreDiscover & Classify Data
Gain full visibility and control by discovering and classifying sensitive data across your data sets.
Enhanced Visibility
Provide comprehensive visibility into enterprise data, covering both data in motion and data at rest through the various technologies within the SSE framework.
Efficient Classification
Offers advanced data classification technologies designed to simplify and enhance the efficiency of data classification.
Learn More

Data Access Governance & Monitoring
Maintain secure data access and implement continuous monitoring to protect sensitive information.
Track Data Usage
Track data usage by analyzing who has access to sensitive data and monitoring their activity. Identify potential external exposure and data leaving enterprise boundaries to prevent unauthorized access and data breaches.
Detect User Activity
Proactively detect anomalies and potential threats in real-time with UEBA. Identify high-risk users by analyzing their behavior and access patterns, and suggest appropriate remediation actions.
Facilitate Compliance & Auditing
Gain full visibility into data exposure risks across your data sets.
Shadow IT Governance
Discover hidden cloud services and assess their compliance risk. Gain visibility into shadow IT usage and the amount of data being sent to these unauthorized applications, allowing you to take action and protect your sensitive information.
Centralized Data Posture Management
Streamline your data security risk management, enabling faster analysis and response to data risks while minimizing the impact on your business.


Proactive Risk Mitigation & Remediation
Stop data breaches before they happen with proactive controls and remediation.
Fix Platform Misconfigurations
Resolve any possible misconfigurations or vulnerabilities in your corporate SaaS and IaaS to secure your data.
Comprehensive Data Protection
Prevent data loss by stopping unauthorized data transfer, whether it's through the web, cloud apps, email, or even new AI applications.
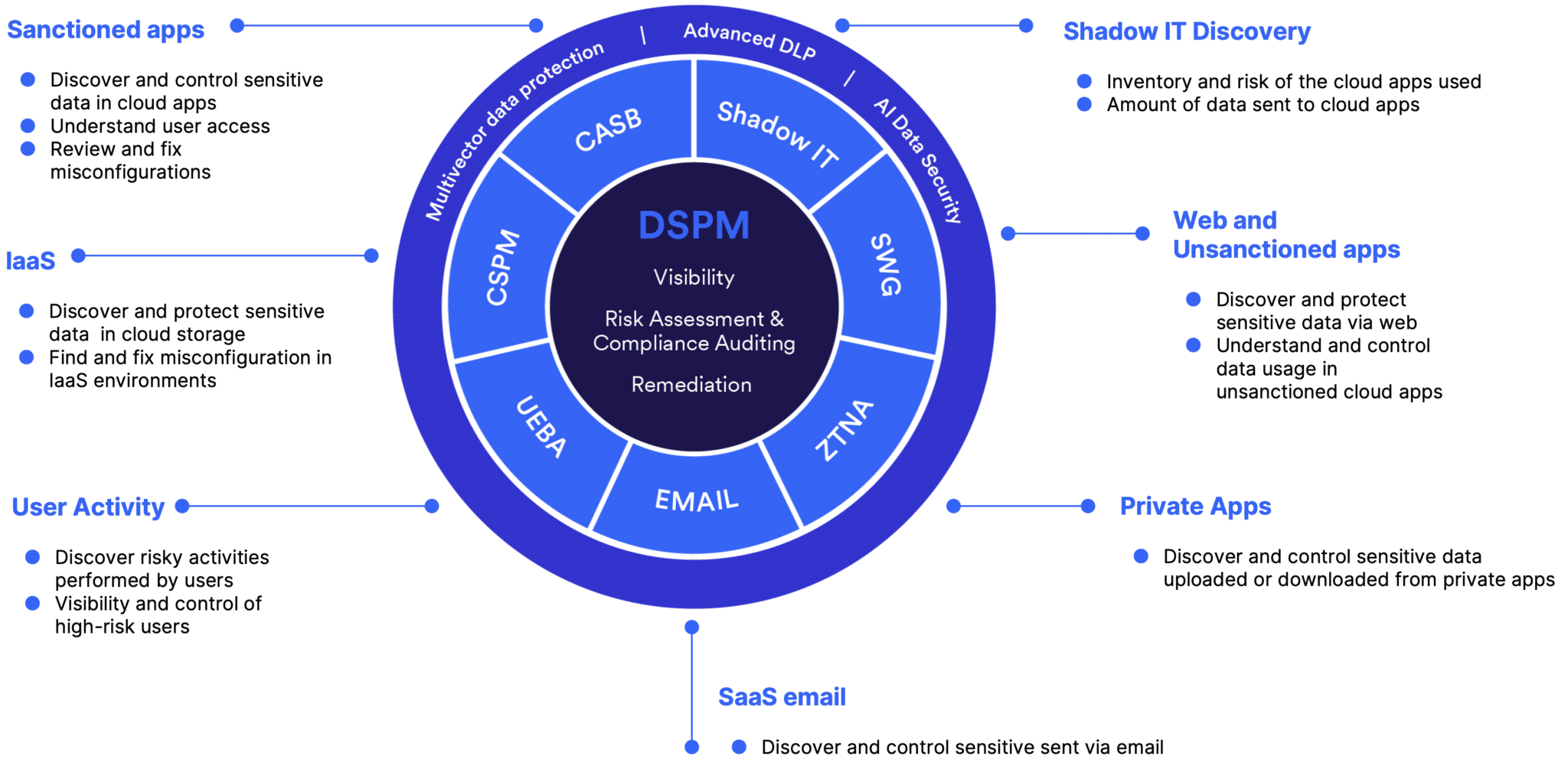
Skyhigh DSPM Benefits
Comprehensive Data Security Approach
Skyhigh’s Secure Service Edge (SSE) solution extends naturally into DSPM by leveraging our strong data security capabilities in AI/ML driven classification, compliance, and threat prevention.
Built on Proven Components
SSE features like SWG, CASB, CSPM, SSPM, UEBA, activity monitoring, and Shadow IT control, provides a seamless DSPM solution without requiring extensive new deployments, all managed from a single console.
Broad Coverage
Skyhigh’s advanced SSE technologies not only provide comprehensive visibility across sanctioned cloud services and infrastructure, but also enable customers to monitor data flowing into Shadow IT services (including GenAI apps) or leaving Private Applications.
Optimized Risk Reduction
Ensure robust data security with automated remediation to prevent data loss and unauthorized access. Leverage policy-based protection to safeguard sensitive data across all enterprise datasets, shadow IT and GenAI apps.
Resources