By Vishwas Manral - Technologist & Head of Cloud Native Security, Skyhigh Security
August 18, 2022 3 Minute Read

I hear a lot of myths about what Zero Trust Network Access (ZTNA) is and how it compares to VPN. Some of it is true, and a lot of it is far from the truth. As I have written the standards around some of the core VPN and security technologies like IPsec/ ADVPN and MPLS, I decided to delve a bit deeper into the technology and do some myth bursting.
Let us try to dive into the core of it – ZTNA vs VPN - what is the fact and the fiction between the two? Let us take a deep dive into the similarities and differences between ZTNA and VPN.
ZTNA reduces the attack surface greatly and prevents lateral movement. As seen in this attack on Cisco, when attackers use lateral movement effectively, it can be very difficult for security teams to detect and that is why ZTNA becomes very critical.
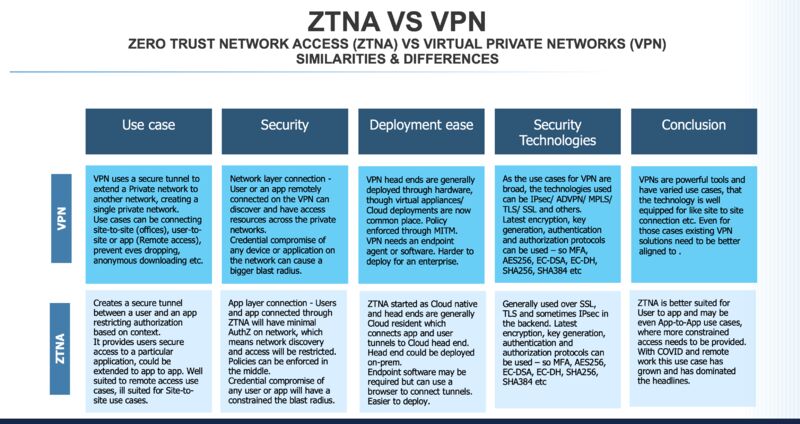
VPN
VPN stands for Virtual Private Networks. VPNs extend private networks across the public internet network. The network can connect at the Data link (Layer-2 or Ethernet) layer, at the Internet (Layer-3 or IP) layer or a transport (Layer-4 or TCP) layer over a tunnel. As an example, when there is a Layer-2 VPN between the two sites, the sites can share the same IP subnet across the public Internet. This leads to a large attack surface, making the service vulnerable. Remote Access VPN is one use case of VPNs where remote users connect with their enterprise devices to enterprise networks and applications over a VPN.
ZTNA
Zero Trust Network Access (ZTNA) creates a least privilege (Zero Trust) model for Remote Access VPNs by allowing a user to connect with applications. ZTNA provides access to applications through a security broker, and the application becomes undiscoverable without the broker. With ZTNA the connection between the user and the application is at an Application (Layer-7) layer allowing the user access to only the application based on context of the device, user and application. Further, the broker can inspect and secure all traffic before it gets to the application.
Asking Tough Questions: Common Myths on ZTNA and VPN
Are ZTNA and Zero trust the same?
No. Zero Trust is a set of architectural principles that are based on “always verify then trust”. ZTNA is the first use case of Zero Trust. It applies the Zero Trust principles to the Remote Access VPN use case. Zero Trust is the “how” while ZTNA is the “what”. We now have use cases for Zero Trust for data access, application access and a lot more.
Is ZTNA better suited for Remote access than VPN?
Yes. The reasons are obvious. ZTNA provides better security, easy scaling out, and smooth onboarding and manageability. With the growth in remote work ZTNA solutions which are cloud provided are easier to scale.
Are VPNs disappearing soon and there are no other use cases of VPNs?
No. VPNs have a lot of different use-cases. These include preventing eves dropping, Site to Site VPNs, anonymous downloading and other non-Remote access VPN use case that ZTNA does not replace them. VPN solutions are generally provided as appliances physical or virtual and are harder to scale out to.
Are ZTNA security algorithms more secure than VPNs?
No. The same encryption, key generation, authentication algorithms can be used for both VPNs and ZTNA. There are no technological differences though there can be differences in the actual implementations.
Isn’t ZTNA mainly about connectivity, secure tunnels and network controls just like VPNs ?
No. Even though ZTNA started out as a replacement for VPN it is a lot more than network centric controls based on identity. ZTNA is becoming more data and security centric. With ZTNA DLP policies can be applied to all outbound files to prevent any malicious or inadvertent data leaks.
Just like VPN, does ZTNA also require ZTNA client to work?
No. ZTNA can be supported in a clientless way and does not necessarily require an agent. For web applications, ZTNA can use browser native capabilities and plugins to create secure connectivity for the end user.
With all the odd misconceptions and fallacious arguments, I have heard concerning ZTNA and VPN solutions, it’s good to look closer at what these solutions accomplish. I hope I have helped in your myth busting of ZTNAs and VPNs!
Back to Blogs