Resources
Enterprise Browsers vs. RBI: Pros, Cons, and Best Fit for the Enterprise
By Tony Frum - Distinguished Engineer
September 11, 2025 8 Minute Read

TL;DR
I once believed Enterprise Browsers (EB) would revolutionize web security—quickly replacing Remote Browser Isolation (RBI), and possibly even Secure Web Gateways (SWG). After working with large enterprise customers and talking to analysts, I’ve changed my perspective. I still believe that EB may fill that role for small and medium businesses, but it may not fit as well in large enterprises.
The promise of Enterprise Browser
I’ve had my eye on the Enterprise Browser (EB) market for a long time. Having worked with Secure Web Gateways (SWG) for the majority of my two decades in the security market, it’s impossible to ignore the novelty of the technology. If you’re not familiar, Enterprise Browsers generally come in two flavors – either browser extensions or entirely new browsers which are forks of the Chromium project. Both options aim to bring new security controls to the browsers in which users spend most of their workday. These controls can include secure remote access to internal applications, specialized anti-malware detection in the browser itself, encryption of locally stored browser data, and more. What intrigued me the most was the data security controls such as clipboard controls, data masking, watermarking pages, screenshot protection, and upload/download controls. In general, pushing controls down to the endpoint instead of trying to implement everything at the network level opens a lot of doors, so this is a powerful new tool in the web security world. If I’m being honest, I originally saw this as a direct threat to the SWG market as a whole.
Remote Browser Isolation
Today, most SWG vendors look to Remote Browser Isolation (RBI) to implement controls in the browser itself. RBI, as the name implies, spins up a browser instance in a remote, isolated environment and loads the page the user requested. Then, the user is able to see and interact with the browser remotely, but none of the page content is loaded on the user’s local machine. Since the RBI solution includes its own browser implementation, controls can be baked into the RBI session that largely mirror what EB solutions are doing today. This closes a lot of gaps in network-based controls such as unreadable content like certificate-pinned apps, Websockets, unreadable encodings, double encryption, and events that only occur locally such as copying and pasting using the local clipboard.
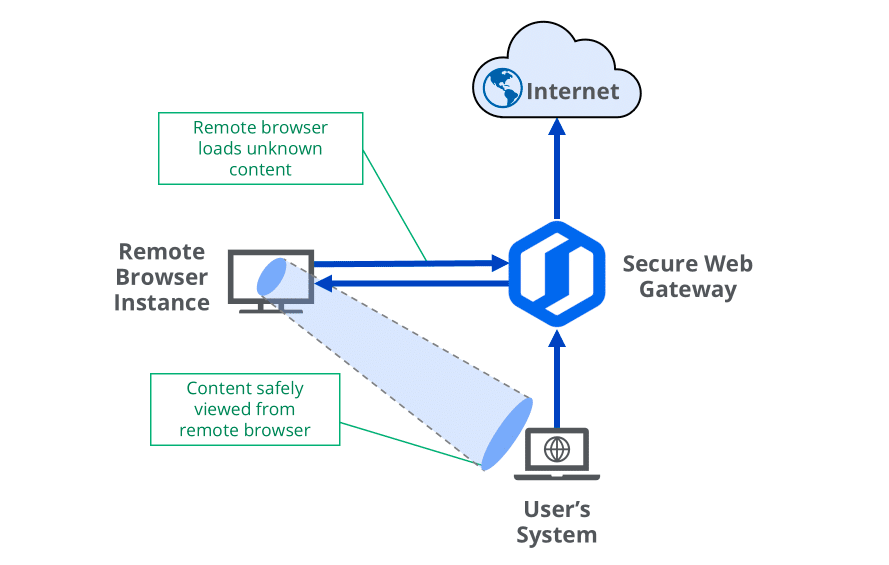
An unexpected perspective from an analyst
My interest in EB drove me to sit down with someone from an analyst firm we partner with and pick his brain about this new technology and some of the vendors in the market. In the course of this conversation he said two things to me that really surprised me. First, he said that EB was “an SMB play” better suited for small and medium businesses than for large enterprises. I work almost exclusively with large enterprises, and I had been thinking very optimistically about what was possible in that context, so this was a bit of a shock to me. As he began to explain this point, he mentioned another thing that took me aback which was the price. Apparently, the average EB purchase costs even more than an RBI solution on a per-seat basis. This seemed impossible to me as offering a cloud-based RBI solution comes with significant infrastructure costs to run all the browser instances and the transit costs of passing the traffic through cloud data centers. EB, on the other hand, does everything locally on the user’s endpoint which comes at near-zero operational cost to the vendor. Try as he might, the analyst couldn’t make either of these things make sense to me. I left the conversation thinking he must be mistaken.
A real-world customer’s dilemma
Fast forward a year or so, and I was asked to meet with a very large customer of ours who has been using our SWG solution for many years. They were considering investing in either adding RBI to their SWG deployment or purchasing an EB solution. Despite what the analyst had told me many months before, I was not optimistic that our RBI solution would be the better option. I had an initial discussion with the customer to clarify their use cases and requirements, and nothing was particularly unique or surprising. They wanted the ability to grant access to “shadow IT” applications while maintaining control over data by implementing upload/download controls, clipboard controls, making pages read-only, and a few other nuanced controls.
Another key use case this customer had, which is very common, was dealing with uncategorized sites. All enterprises have to contend with this classic catch-22 of determining how to handle sites that are uncategorized. If you block them, then you end up with an increase in help desk tickets because no vendor’s categorization is perfect, so you’ll inevitably block some legitimate sites. On the other hand, if you allow them, then you’re opening yourself up to a great deal of risk because the majority of threats out there will come from uncategorized sites. Companies almost always need a way to allow uncategorized sites while maintaining security, and that’s what this customer needed.
Throughout my engagement with this large enterprise customer, I was forced to weigh the pros and cons of these two technologies from their perspective. Conversely, because of the analyst’s comments, I would continually consider things from the perspective of a small business. Ultimately, I came to realize that I was wrong and the analyst had been absolutely right!
A small business’s perspective
Put yourself in the shoes of a small business of 50-100 employees and consider the challenge of deploying a SWG solution. Such an organization is most likely looking for some very basic controls and a basic level of security. They may have an “IT guy” with some basic knowledge but no serious networking or security expertise. Their infrastructure may lack some key components that are necessary for a successful SWG deployment as well. Now, contrast that with EB. It would be pretty straightforward to push out a new browser app to 100 endpoints, and it could not only eliminate your need to deploy SWG and RBI but also a Zero-Trust Network Access (ZTNA), or “Private Access”, solution. This represents a simple, effective alternative to SWG and, possibly, RBI and ZTNA which might justify such a high price point for a relatively small user base.
A large enterprise’s reality
Now consider this from the perspective of an enterprise with hundreds of thousands of endpoints, a team of networking experts, a team of security experts, and all the infrastructure that goes along with being a huge enterprise. This changes things entirely. First, let’s assume that such an organization did deploy an EB solution. Deploying to, potentially, hundreds of thousands of endpoints is no small task and hundreds of thousands of users would have to be educated to use this new browser. Additional controls may also have to be in place to prevent them from using non-enterprise browsers for sites where EB controls need to be applied.
Another thing you might not consider is that large enterprises tend to standardize on a single browser such as Google Chrome, and part of their procurement process is to ensure that all the tools they acquire support their chosen browser. How are they to do this with an obscure EB solution? Does Jira officially support my EB of choice? What about the hundreds of other tools our organization uses? This quickly becomes untenable. What’s worse,a large enterprise can’t simply ignore non-browser based HTTP traffic such as requests from a thick client like Microsoft Teams, Google Drive, Slack, and others. This means that even if the EB solution did solve a lot of their use cases, they cannot use it as a SWG replacement.
Okay, what if this customer were to deploy RBI instead of EB to achieve their use cases? Deployment would certainly be more straightforward because RBI is basically just a feature of SWG which they already have. If you’re using any SWG solution worth its salt, deploying RBI should be a simple process of purchasing a license and enabling the feature. Your endpoints are already sending their web traffic to the SWG, so there’s no need to touch your many thousands of endpoints. Your users won’t need much education, if any, for your RBI solution as they are typically designed to be very transparent to the user. Even if you want the user to know what’s happening, it’s usually an option to present the user with a customized pop-up explaining that they’re using an isolated session and what controls might be applied. If your SWG solution uses cloud-based RBI, as many do, then no infrastructure changes are required. Since RBI is generally used in a selective way, you likely won’t apply it to your trusted applications used by your organization which probably relieves you of the need to test these tools in your RBI solution.
Bulletproof malware protection
One last thing to consider is the catch-22 uncategorized website problem that most large enterprises need to solve. Enterprise Browsers bring improvements to web security by looking for web threats within the browser DOM itself. This allows them to find obfuscated threats after they’ve been delivered and deobfuscated within the DOM. This definitely provides an elevated level of protection for all content loaded in the EB. However, RBI fully isolates the endpoint from the website content. It’s not elevated protection. It’s basically bulletproof protection against malware. Sure, the user can still be tricked by social engineering, but that can be addressed by coaching the user that a page is risky, making the page read-only, preventing uploads or logins, and other similar controls. However, there’s basically no way the endpoint can be compromised by malware via RBI. This empowers customers to allow, but isolate, uncategorized websites without increasing their risk of compromise.
Contractors and 3rd-party access
At this point, you may think to yourself, “This guy is ignoring the third-party contractor scenario,” which is a common use case for EB. The third-party contractor use case is where you may want to grant a user from outside your company the ability to access your internal, private applications from a device that isn’t managed by your company. You want to grant this access while being able to secure your data and restrict their access to only what they need. Yes, that’s an additional consideration, but this same EB vs. RBI paradigm exists in that situation, too. Most fully-featured ZTNA solutions like ours offer “clientless” access to private applications, and they can also apply RBI to these clientless sessions to push data access controls down to an unmanaged endpoint as well. This is simpler and more seamless than asking a third-party individual to install an additional browser application or extension in order to access data.
Data classification and awareness
One final consideration is that of data classification and awareness. EB solutions are still a somewhat nascent technology, and the vendors do not generally have advanced data classification capabilities. Most use a relatively rudimentary regular expression-based approach to data classification. Mature SSE vendors who offer SWG and RBI, however, tend to have much more robust technologies such as Exact Data Match (EDM), Indexed Document Matching (IDM), Optical Character Recognition (OCR), AI-based classification, and more.
Customers tend to be heavily invested in these classification mechanisms and have already implemented mature processes around data classification and incident management in these solutions. This data awareness is often available within isolated sessions which is why the native RBI capability of an incumbent SSE solution might be more attractive than a disjoint EB solution.
Conclusion
In the end, as is often the case, being forced to see our technology through the lens of the customer I learned things I otherwise wouldn’t have. Enterprise Browsers are a really innovative technology with a lot of promise, and I’m excited to see where the technology goes. However, for the large enterprise it’s pretty clear that RBI is often going to be the better option at least for the time being.
About the Author

Tony Frum
Distinguished Engineer, Product Management
Tony is a Distinguished Engineer at Skyhigh Security. Starting at McAfee in 2005, he has over 20 years of experience in the security industry specializing in Secure Web Gateway, Cloud Access Security Broker and Data Loss Prevention technologies.
Related Content
Trending Blogs
LLM Attributes Every CISO Should Track Today
Sarang Warudkar February 18, 2026
From DPDPA Requirements to Data Visibility: The DSPM Imperative
Niharika Ray and Sarang Warudkar February 12, 2026
Skyhigh Security Q4 2025: Sharper control, clearer visibility, and faster action across data, web, and cloud
Thyaga Vasudevan January 21, 2026
The Hidden GenAI Risk That Could Cost Your Company Millions (And How to Fix It Today)
Jesse Grindeland December 18, 2025
Skyhigh Security Predictions: 2026 Is the Year AI Forces a New Blueprint for Enterprise Security
Thyaga Vasudevan December 12, 2025