Resources
Data Overload to Actionable Intelligence: Streamlining Log Ingestion for Security Teams
By Megha Shukla and Pragya Mishra -
September 18, 2025 7 Minute Read

“Great things are done by a series of small things brought together.” — Vincent Van Gogh
While open to interpretation, the quote reflects a fundamental truth: in today’s cybersecurity landscape, logs are not optional, they serve as the backbone of security operations, providing the data needed for threat detection, visibility, and rapid response to keep your enterprise secure and resilient.
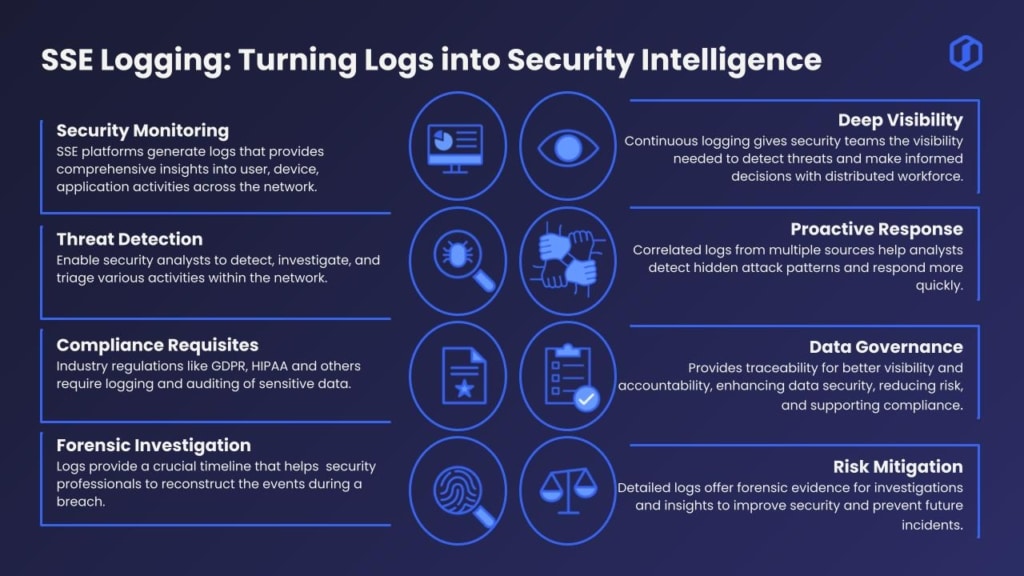
In a Security Service Edge (SSE) framework, logging plays a pivotal role. It’s not about collecting data for the sake of it. It’s about creating real-time insights that help teams understand what is happening across users, devices, and applications, 24/7. That visibility is essential. Even a brief delay can allow threats to spread laterally, sensitive data to leak, or compliance gaps to emerge.
Logs are simultaneously gathered from multiple SSE vectors. By centralizing these streams, your enterprise can connect the dots between products and solutions, uncover hidden threats, and act swiftly before damage is done.
Security teams leverage tools like SIEM and XDR to analyze logs for identifying threats and driving incident response. Compliance teams depend on these logs to demonstrate adherence to regulations such as GDPR and HIPAA. Threat hunters proactively sift through them to uncover risks before they escalate. At the core, centralized logging is what enables these efforts—providing the visibility and context needed for effective security and governance. Below is a brief overview of the logging framework and the value it delivers.
But of course, this is all familiar ground. We are not here just to rehash the basics.
Today, we want to explore a few scenarios on how Skyhigh SSE Logging, also known as Skyhigh Log Streaming, has helped real-world global leaders, from food and industrial sectors to telecommunications and chemical manufacturing, boost their security posture and confidently embrace secure, cloud-first operations.
1. Engineered to Handle High Demand
In today’s fast-paced digital world, logging systems can quickly become overwhelmed. When thousands of log entries flood in every second, pipelines can choke under throughput limits, parsing delays, or network throttling. The result? Threats go undetected, blind spots multiply, and security teams are left scrambling.
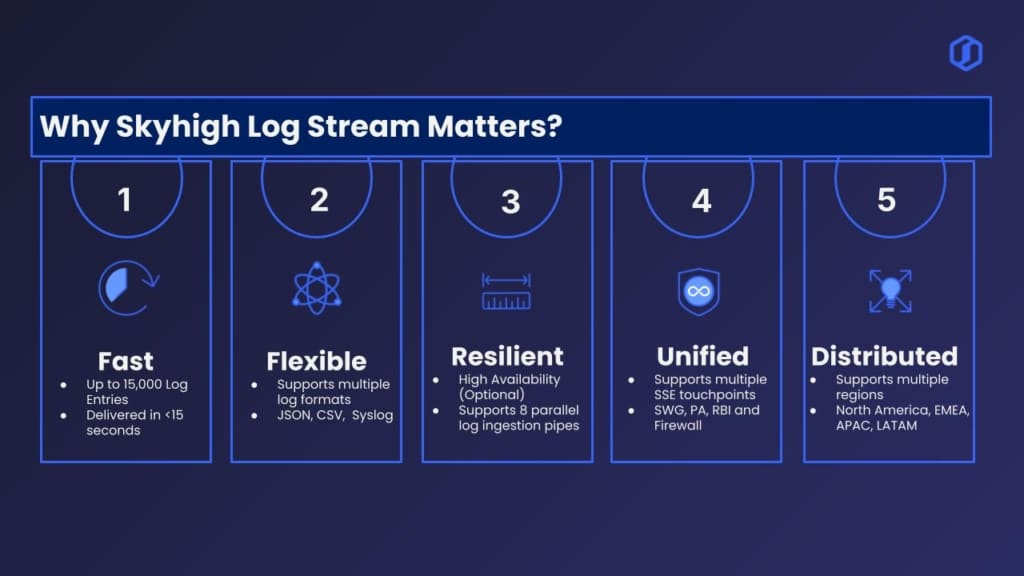
That’s where Skyhigh Log Stream comes in. Engineered to scale effortlessly, it can process more than 15,000 log entries in under 15 seconds, ensuring your security stays sharp even during the busiest moments. Here’s how it makes a difference:
- Instant Threat Detection: Logs are ingested in real time, so anomalies and breaches are flagged as they happen, not minutes later. This rapid response helps teams contain threats before they spiral out of control.
- Scalable Operations: The ability to process 15K+ log entries in under 15 seconds means the system can scale with business, when support for thousands of remote users, cloud apps, or global infrastructure, is the ask. It effectively helps prevent log ingestion backlogs during peak usage (DDoS, malware outbreak, login storms).
- Stronger Compliance and Forensics: Logs are processed continuously and accurately, providing the detailed audit trails required for regulations like GDPR, HIPAA, or SOX. Investigations are faster, cleaner, and more reliable when every event is captured in real time.
2. Support for Diverse Log Formats
Today’s IT environments are highly complex, with a diverse mix of systems, applications, and tools. This diversity makes it impractical to enforce uniform log formats at the source. Without standardized log entries, data fragmentation becomes a major challenge, slowing down ingestion pipelines, complicating event correlation, and sometimes requiring separate processing logic for each data source. During incidents, teams may be forced to reverse-engineer poorly structured logs, adding delays and increasing operational overhead.
Skyhigh Log Stream solves this challenge by supporting multiple log formats – JSON, CSV, Syslog, ensuring seamless integration and normalization across the board. This approach addresses challenges related to scalability, correlation, and data consistency, along with following few other benefits:
- Seamless Integration: Logs from any source, be it modern or legacy can be ingested without rewriting mechanisms, making onboarding faster.
- Interoperability with Tools: Aligning log formats across SIEM, SOAR, analytics platforms, and compliance tools simplifies workflows and avoids costly custom connectors.
- Tailored Logging for Teams: Different teams have different needs, from debugging to compliance audits. Flexible formats allow logs to be structured for specific use cases, increasing their utility.
3. High Availability for Mission-Critical Operations
Log pipelines are the nervous system of security and monitoring. If they go down whether due to environmental factors, maintenance, or unexpected disruptions, the impact is serious: visibility is lost, dependent systems (SIEM, SOAR) falter, breaches go undetected, and compliance failures are a sure shot.
Skyhigh Log Stream tackles these risks by offering the option to deploy your Enterprise Connector (EC) in High Availability (HA) mode. You can choose to enable HA based on your operational needs, ensuring flexibility without compromise. In HA mode, log entries continue to flow seamlessly even if one EC experiences downtime, providing uninterrupted data ingestion. Following are few other benefits:
- Stronger compliance posture with immutable audit trails: Continuous log collection ensures data integrity, audit readiness, and compliance. HA mode captures logs in real-time, minimizing risks of violations, audit failures, and penalties.
- Better Observability and Monitoring: Real-time, uninterrupted log access ensures security tools have full visibility during failures, eliminating blind spots for faster threat detection and monitoring across complex environments without data gaps.
- Automated, Event-Driven Response: Logs enable automated event-driven workflows like auto-scaling and alerts, reducing manual effort and risks. Continuous availability of accurate data also supports advanced use cases like anomaly detection and predictive maintenance.
4. Unified Logging Across Distributed SSE Vectors
ZTNA, SWG, CASB, and DLP each generate critical data, but without centralized aggregation, security teams are left piecing together fragmented information, delaying detection and responding effectively to threats.
Skyhigh Log Stream centralizes data from all these vectors, namely – Secure Web Gateway (SWG), Private Access (PA), Remote Browser Isolation (RBI) and Firewall, helping teams:
- Improve Data Quality: Aggregation allows for normalization and enrichment of logs, creating a consistent data format that simplifies downstream processing, improving the accuracy of security insights.
- Streamline Alerts: Consolidation of alerts from different SSE vectors, also reduces alert fatigue and improves prioritization.
- Enhance Training and Simulations: Centralized logs allow for realistic incident simulations, helping teams prepare for real-world attacks.
5. Simplifying Global Log Ingestion with Multi-Region Support
For enterprises with a global footprint, operating offices and data centres across continents, centralizing log data into a single platform seems like the ideal approach. In practice, however, it often comes with significant challenges. Transmitting logs across long distances introduces latency, resulting in delays that compromise real-time monitoring. The infrastructure needed to support centralized logging like VPN’s, cloud routing can be costly. Managing these across different time zones, network conditions, and regional infrastructures adds layers of complexity. On top of that, compliance concerns arise when logs are transmitted outside mandated geographic boundaries, potentially violating data sovereignty laws like GDPR and exposing enterprises to hefty fines and legal repercussions.
Skyhigh Log Stream addresses these challenges head-on with its multi-region support and 8 parallel log ingestion pipelines, enabling seamless, real-time, simultaneous log streaming from locations around the world. With regional coverage spanning North America, EMEA, APAC, and LATAM, organizations can confidently monitor their environments wherever their users and services operate. Resulting in:
- Better Threat Detection: Skyhigh Log Stream ingests logs from multiple regions simultaneously, enabling security teams to correlate cross-geographic attacks, enhance detection accuracy, and speed up response times.
- Low Latency and Faster Ingestion: Processing logs closer to where they are generated, minimizes latency, delivering faster ingestion, real-time visibility, and quicker incident response.
- Cost Optimization: Local processing reduces cross-region data transfer costs, helping avoid expensive bandwidth charges and cloud egress fees.
To sum it up following is a recap on how Skyhigh Log Stream can make a difference for you:
Skyhigh Log Stream empowers your enterprise to tackle scale, complexity, and compliance challenges by turning fragmented data into actionable insights. It offers fast, reliable and flexible logging to support demand spikes, global operations, diverse environments, and uninterrupted monitoring. With real-time visibility and seamless security integration, you are better equipped to detect threats, stay compliant, and confidently secure cloud-first future. This is not just about logs, it is about deriving maximum value from the whole process.
If you would like to know more about how Skyhigh Log Stream can make a difference for your enterprise, please reach out.
About the Authors

Megha Shukla
Sr. Product Marketing Manager
Megha is a cybersecurity product marketer by trade and a tech-jargon translator by passion. She specializes in bridging the gap between what engineers build and what customers actually care about, without drowning it in buzzwords.
With a background that spans product marketing, customer marketing, competitive intel, product management, business development, channel strategy, and account management, she’s worn just a few hats the cybersecurity and IT world has to offer (some at the same time).
Whether she’s launching a new product, defining go-to-market strategy, or writing a blog post that says what others won’t, she brings clarity, curiosity, and a healthy respect for what can (and should) be said out loud.

Pragya Mishra
Product Manager
Pragya Mishra is a Product Manager for CASB and Shadow IT at Skyhigh Security. Driving initiatives that help enterprises gain comprehensive visibility into unsanctioned and AI-driven applications, proactively managing Shadow AI risks by integrating LLM-based detection into Shadow IT management while strengthening their security posture. Through Skyhigh’s newest Log Stream, she helps enterprises to stream high-fidelity logs into their existing SIEM and analytics tools for faster threat detection and response. She also leads efforts in identity provisioning and role-based access control (RBAC), ensuring automated and secure user lifecycle management across large enterprises.
Her expertise spans competitive analysis, user research, and the design of scalable dashboards and UI components for global enterprise environments. Over the years, she has also championed advanced unified platform capabilities that deliver actionable insights, improved governance, and measurable customer value.
Related Content
Trending Blogs
LLM Attributes Every CISO Should Track Today
Sarang Warudkar February 18, 2026
From DPDPA Requirements to Data Visibility: The DSPM Imperative
Niharika Ray and Sarang Warudkar February 12, 2026
Skyhigh Security Q4 2025: Sharper control, clearer visibility, and faster action across data, web, and cloud
Thyaga Vasudevan January 21, 2026
The Hidden GenAI Risk That Could Cost Your Company Millions (And How to Fix It Today)
Jesse Grindeland December 18, 2025
Skyhigh Security Predictions: 2026 Is the Year AI Forces a New Blueprint for Enterprise Security
Thyaga Vasudevan December 12, 2025