Resources
INTELLIGENCE DIGEST
It may only take one attack to get stung by OneNote!
Threat actors weaponize Microsoft OneNote documents for malware delivery
By Rodman Ramezanian - Global Cloud Threat Lead
March 15, 2023 7 Minute Read
Part of Microsoft’s extensive 365 application suite, Microsoft OneNote offers users a powerful yet flexible information management workbench. As organizations continue their rampant surge into the cloud, OneNote presents a useful notetaking and task management bridge between corporate premises, BYOD, and enterprise cloud realms. Thanks to the wide adoption of OneNote, however, attackers have turned their attention to the app as a viable route for malware distribution.
Security research from the likes of BleepingComputer, Trustwave, and Sevagas has discovered that threat actors are increasingly embedding files into OneNote documents and tricking users into executing them. Shockingly, it wasn’t until late-2022 that attachments within OneNote were exempt from Microsoft’s native Mark of the Web (MOTW) labelling regime, which is effectively designed to notify Windows OS, applications, and end-users that the file originated from the web and shouldn’t be trusted by default.
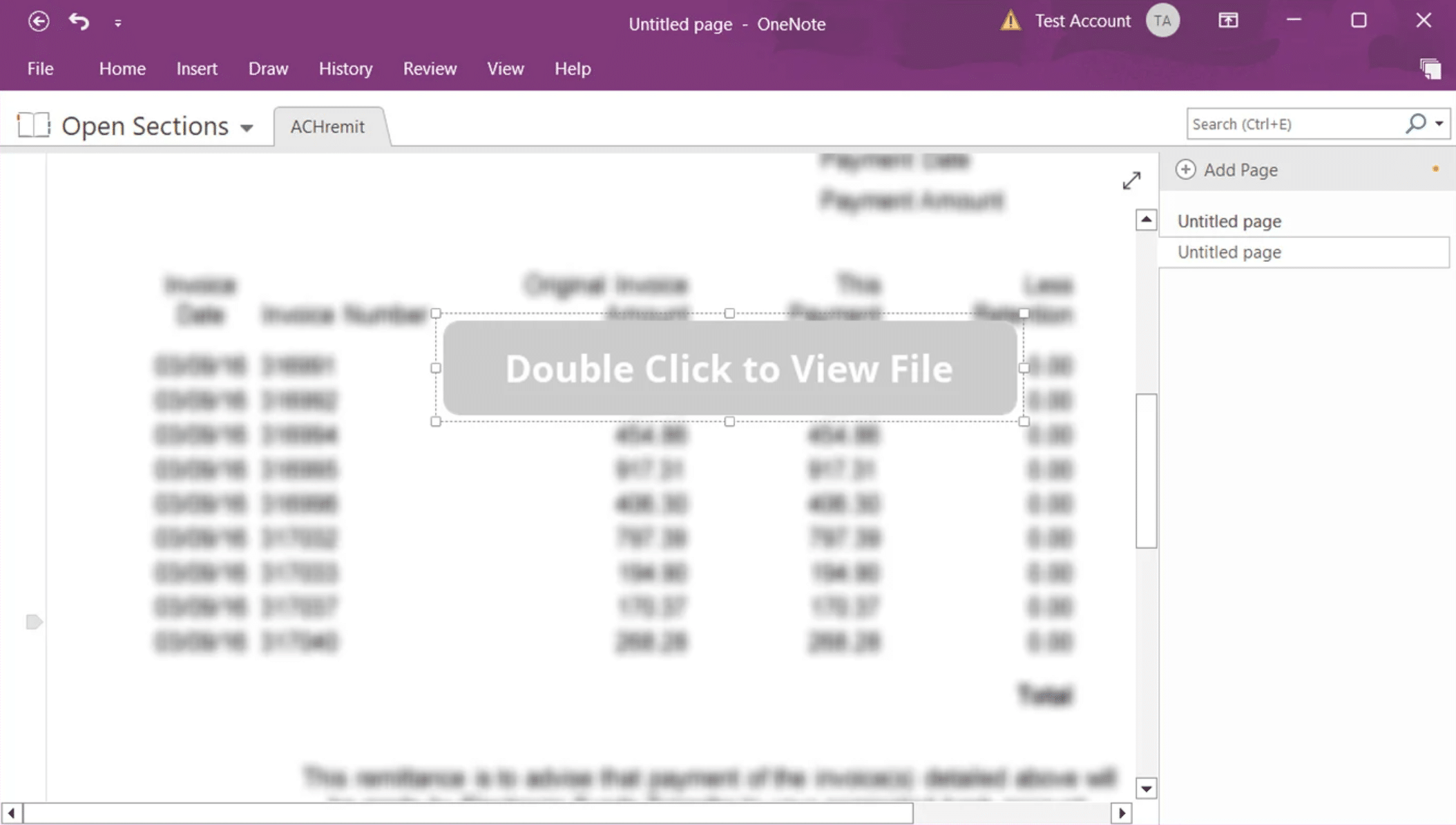
While this MOTW labelling issue appears to have been silently patched by Microsoft at time of writing – greatly minimizing the risks associated with .one files – it unfortunately does not eliminate the risk completely. Threat actors can embed a wide range of file types within infected OneNote documents, including but not limited to Visual Basic Script (VBS) payloads as seemingly innocuous attachments. Using social engineering, the attachments disguise themselves as legitimate content for businesses, including invoices, mechanical drawings, DHL shipping notifications, remittance forms, and other documents. The files, however, launch malicious scripts once users are convinced to double-click on the embedded malware within the notebook.
Why do these breaches occur?
In the quest to fuel productivity, accessibility, and collaboration, organizations embrace native applications like Microsoft OneNote to empower their workforces.
When software companies like Microsoft update their products to prevent nefarious uses, threat actors naturally shift their focuse and tradecraft to develop newer attack techniques offering stronger efficacy.
Attacks abusing OneNote for malware delivery are, in fact, quite similar to those leveraging other forms of infected Office files: the user is lured into opening the document and disabling security checks, resulting in the execution of malicious code.
What makes these attacks particularly effective for cybercriminals is that the targeted user physically interacts with the infected document that’s laced with convincing traps. After all, even though opening the malicious attachment may generate a warning dialog, there is still a high risk that users will ignore it.
For example, attackers use fake graphical buttons in their OneNote files (very much like the native Windows clickable buttons) that would seemingly download the requested document, but when clicked, run the embedded malware script instead.
Unfortunately, social engineering also plays a big role in the effectiveness of these campaigns, with victims continuing to be misled and duped into executing that initial payload and foothold for the perpetrators.
What can be done?
As always, cautiously vetting incoming emails and instant messages is highly recommended. After all, files like these can be distributed very easily thanks to the interweaving of collaboration platforms like Microsoft 365. The same vigilance must be applied to web browsing activity, since fraudulent and risky content online can facilitate the dropping of malware payloads.
Considering, also, the fact that .one file attachments are infrequently used nowadays and considered somewhat unusual or suspicious, recommendations circulating the intelligence community suggest blocking .one file extensions until further notice.
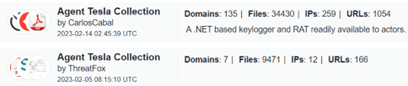
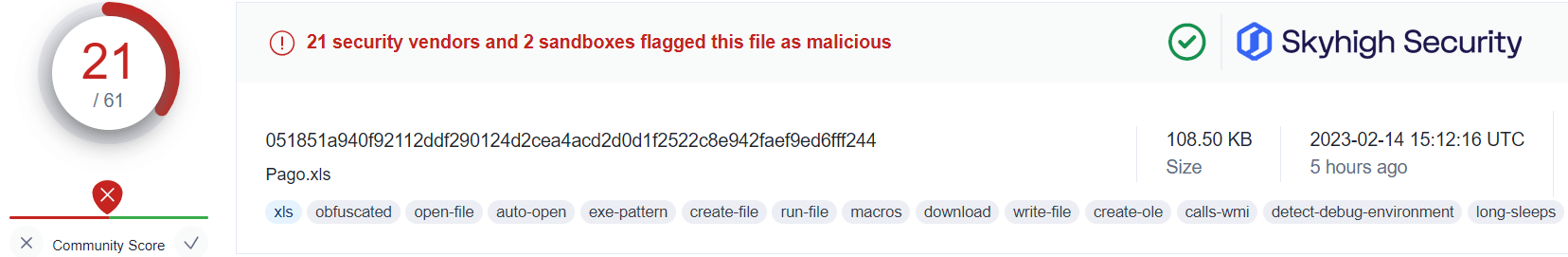
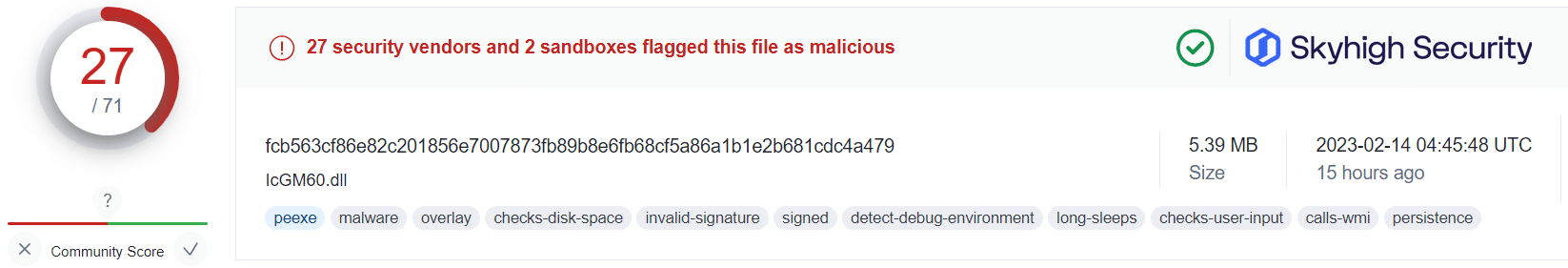
Recent industry research suggests an increasing number of malware campaigns abuse OneNote documents for the delivery of malware, such as AgentTesla, Quasar RAT, Qbot/Quakbot, and DoubleBack, among many others.
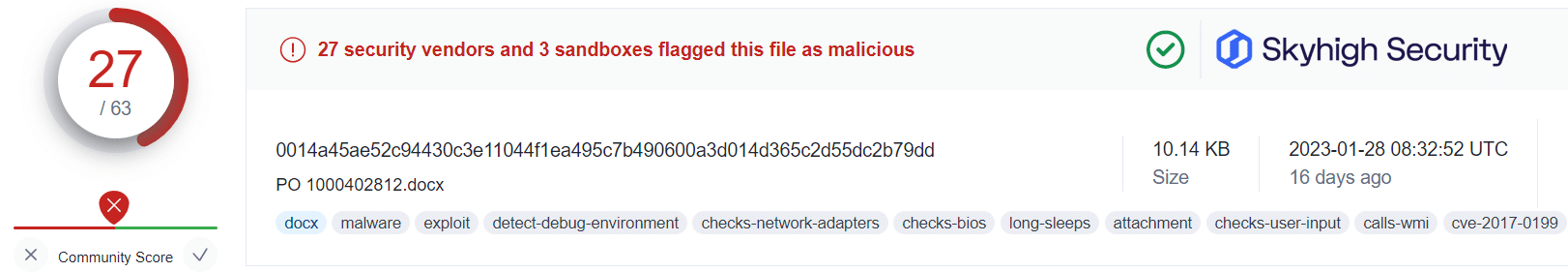
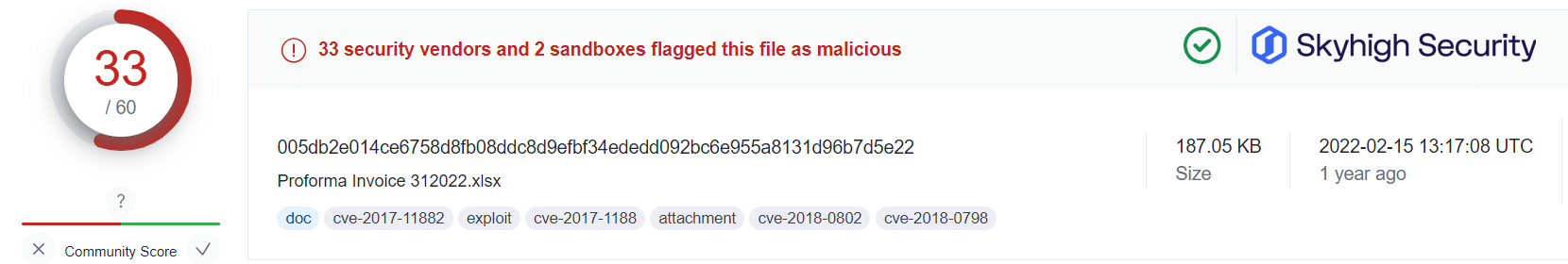
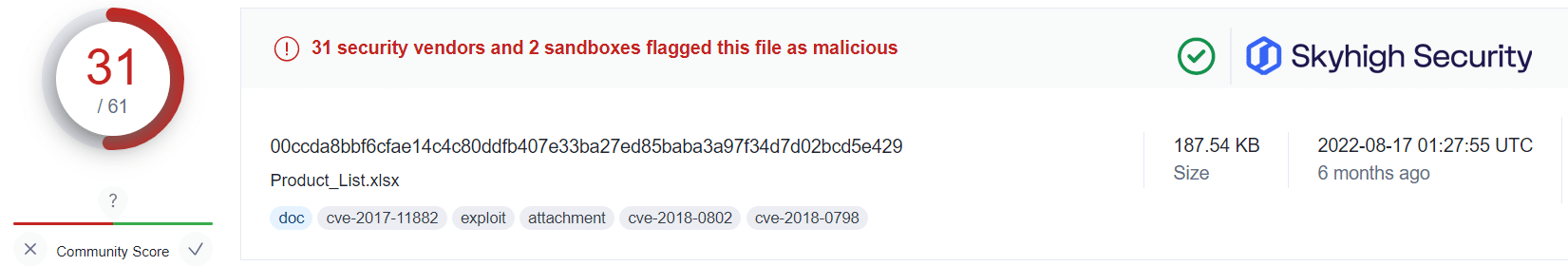
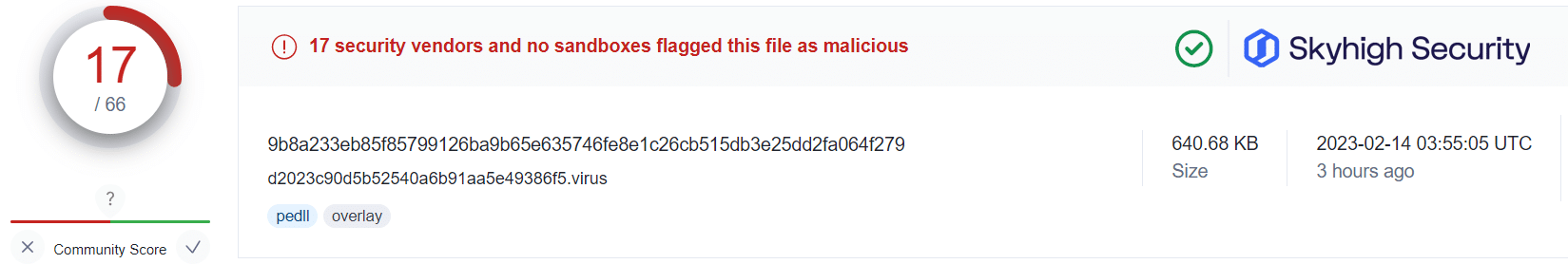
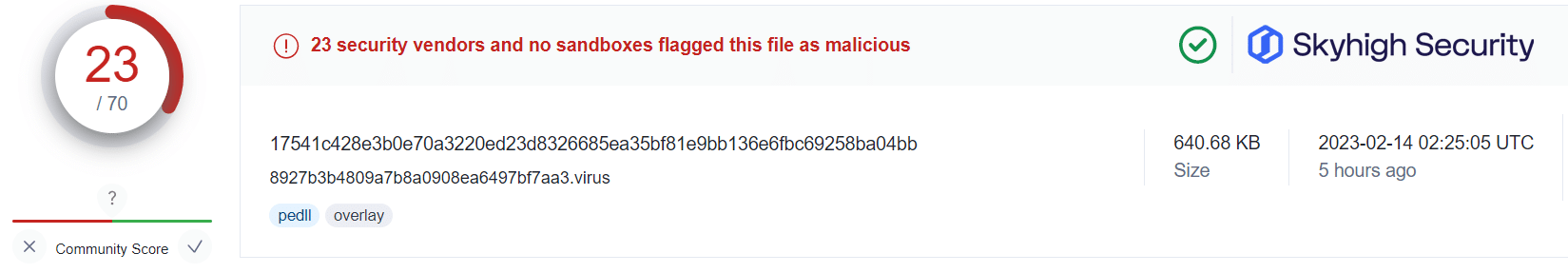
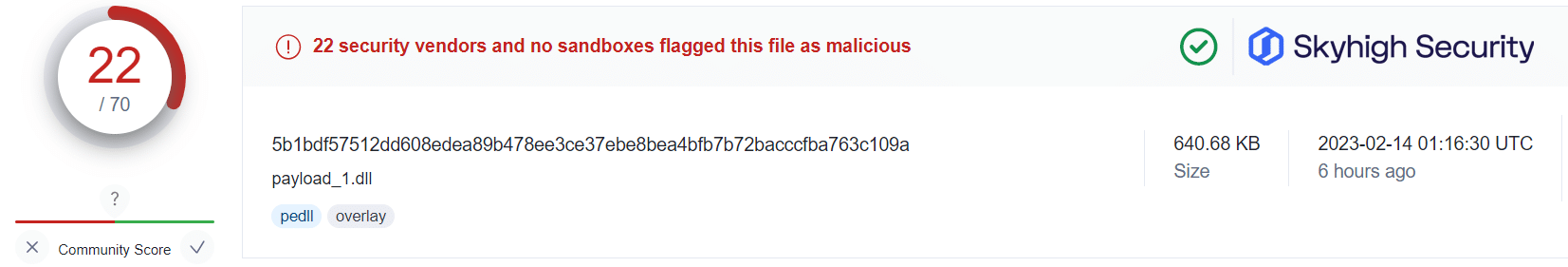
Applying this information alongside the public VirusTotal database, and using randomized sampling of hashes associated with those campaigns, we are presented with some insightful findings:
What this tells us is that even in cases where users have fallen victim to the malicious OneNote attachment, Skyhigh Security’s Gateway Anti-Malware (GAM) emulation and heuristics engine (formerly named McAfee-GW-Edition as shown in VirusTotal) has been able to identify and prevent the malware-ridden payloads from being retrieved from the attacker’s servers.
This is not to suggest that users should freely download and open OneNote attachments without caution. However, it does provide additional assurance that in the unfortunate case of a user being duped, Skyhigh Security’s analysis engines are able to identify and convict the associated threats before any further harm by the threat actors.
For existing Skyhigh Security customers, the Gateway Anti-Malware (GAM) engine is natively converged within its Security Service Edge (SSE) platform, enabling it to be utilized for a wider range of use cases and scenarios involving web and cloud content as well.
Based on the organization’s risk appetite, security teams can also leverage Skyhigh Security’s Remote Browser Isolation technology to render OneNote documents online if required, allowing for only a visual stream of pixels to be presented to the user without allowing the OneNote file to execute on the local device itself. In so doing, the user’s device is effectively shielded from any threats contained within the document or its attachments.
As always, however, the best advice remains to stay vigilant and protect your systems and users by only opening messages and attachments from trusted parties.
References:
VirusTotal Sample Analysis – AgentTesla, QuakBot, Quasar RAT campaigns
https://www.virustotal.com/
BleepingComputer
https://www.bleepingcomputer.com/news/security/hackers-now-use-microsoft-onenote-attachments-to-spread-malware/
Use Skyhigh Security?
- Enable Gateway Anti-Malware engine for emulation and analysis of file-based and fileless payloads
- If your organization enables it, send users to a Remote Browser Isolated session to render the OneNote document, thereby shielding the device from any contained threats
- Apply Web DLP rules to limit or block the downloading of specific file types, such as OneNote (.one) documents
- If users browse to risky websites to retrieve OneNote files, block downloads and other specific activities using Remote Browser Isolation
With over 11 years’ worth of extensive cybersecurity industry experience, Rodman Ramezanian is an Enterprise Cloud Security Advisor, responsible for Technical Advisory, Enablement, Solution Design and Architecture at Skyhigh Security. In this role, Rodman primarily focuses on Australian Federal Government, Defense, and Enterprise organizations.
Rodman specializes in the areas of Adversarial Threat Intelligence, Cyber Crime, Data Protection, and Cloud Security. He is an Australian Signals Directorate (ASD)-endorsed IRAP Assessor – currently holding CISSP, CCSP, CISA, CDPSE, Microsoft Azure, and MITRE ATT&CK CTI certifications.
Candidly, Rodman has a strong passion for articulating complex matters in simple terms, helping the average person and new security professionals understand the what, why, and how of cybersecurity.
Attack Highlights
- With Microsoft disabling macros in downloaded MS Office documents, hackers have had fewer opportunities to execute code on targeted systems. OneNote attachments in phishing emails are becoming increasingly popular as a new attack vector.
- OneNote documents serve as powerful tools for threat actors, since until recently, they did not benefit from Microsoft’s Mark-of-the-Web (MOTW) protection, and they allowed files to be attached in OneNote notebooks and then executed with little user warnings.
- Since Microsoft OneNote is installed by default in most Microsoft Office/365 deployments, even though a Windows user may not use the application, it is still available to open the one file format.
- Once executed, the embedded script runs commands on the host system to download the attacker’s infected files for initial remote access.
- The user is then shown a decoy file that looks like the expected document. In the background, however, a malicious batch file installs the malware payload on the device.