Hot on the heels of numerous high-profile breaches at the hands of cybercrime gangs, Cisco undoubtedly takes no pleasure in confirming a breach of its corporate network in a recent extortion attack from the Yanluowang ransomware group.
With industry reports confirming a successful compromise of a Cisco employee’s credentials as a trigger, the news serves as yet another stark reminder of how destructive remote access abuse can be.
 Figure 1. Yanluowang Ransom Threats. Source: Twitter
Figure 1. Yanluowang Ransom Threats. Source: Twitter
In this instance, the initial abuse of Cisco VPN was aided by stolen corporate credentials from within the Cisco employee’s personal Google account.
Once authenticated (thanks to further social engineering and voice phishing techniques), the attackers acquired access into Cisco’s corporate networks, enrolled a number of devices for Multi-Factor Authentication, and ultimately exfiltrated data for purposes of ransom and extortion.
Yet again, much like the Tactics, Techniques, and Procedures (TTP) used by similar groups like Lapsus$ and UNC2447, we see authenticated remote access via VPN being a critical threat vector aiding the data theft. The Yanluowang group claims to have stolen approx. 2.8GB of data.
As stated by Cisco’s own security teams, the attacker then escalated privileges to administrator level, allowing them to maneuver inside the network and login successfully to multiple systems. Herein lies the critical risk of lateral movements facilitated by unrestrained VPN access.
Why do these breaches occur?
Hybrid workforces blurring lines between personal cloud apps and business apps present unique challenges and increased risks. Unfortunately, these aren’t the sorts of risks that can be mitigated with a few different point products either!
Social engineering and phishing techniques employed by cyber criminals are nothing new. However, the continuing trend of corporate employees being duped by convincing schemes cannot be discounted.
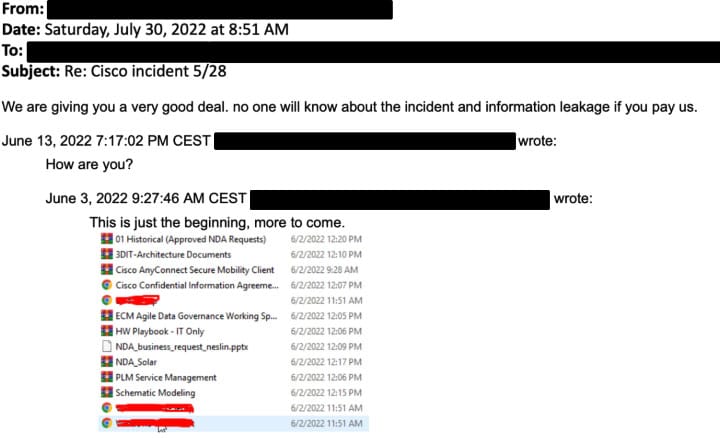 Figure 2. Ransom correspondence from attackers to Cisco staff. Source: Twitter
Figure 2. Ransom correspondence from attackers to Cisco staff. Source: Twitter
As hybrid workforces continue to grow, attackers increasingly set their sights on obtaining remote access credentials. Why? A vast majority of enterprises are yet to abandon their traditional VPN technologies that grant unfettered access to corporate environments once authenticated.
Once these attackers acquire the necessary remote access tools and credentials, they’ll typically then divert their efforts towards deceiving victims using social engineering tactics to bypass Multi-Factor Authentication checks that usually follow.
Traditional Virtual Private Network (VPN) introduces the risk of excessive data exposure, as any remote user with valid login keys can get complete access to the entire internal corporate network and all resources within.
Just as hybrid workers will typically agree when working remotely, you can bet the threat actors are well aware of how valuable remote access is!
In the context of this incident involving Cisco, it’s clear to see how harmful compromised remote access, lateral movements, and privilege misuse can be to even the largest technology firms.
What can be done?
Given the threat actor’s proven competence in using a wide range of tactics to obtain initial access, user education is a vital requirement for countering Multi-Factor Authentication bypass techniques.
Considering the attacker’s misuse of administrative privileges, apply strong device checks by enforcing stricter controls to limit or block enrollment and access from unmanaged or unknown devices to corporate apps, networks, and services.
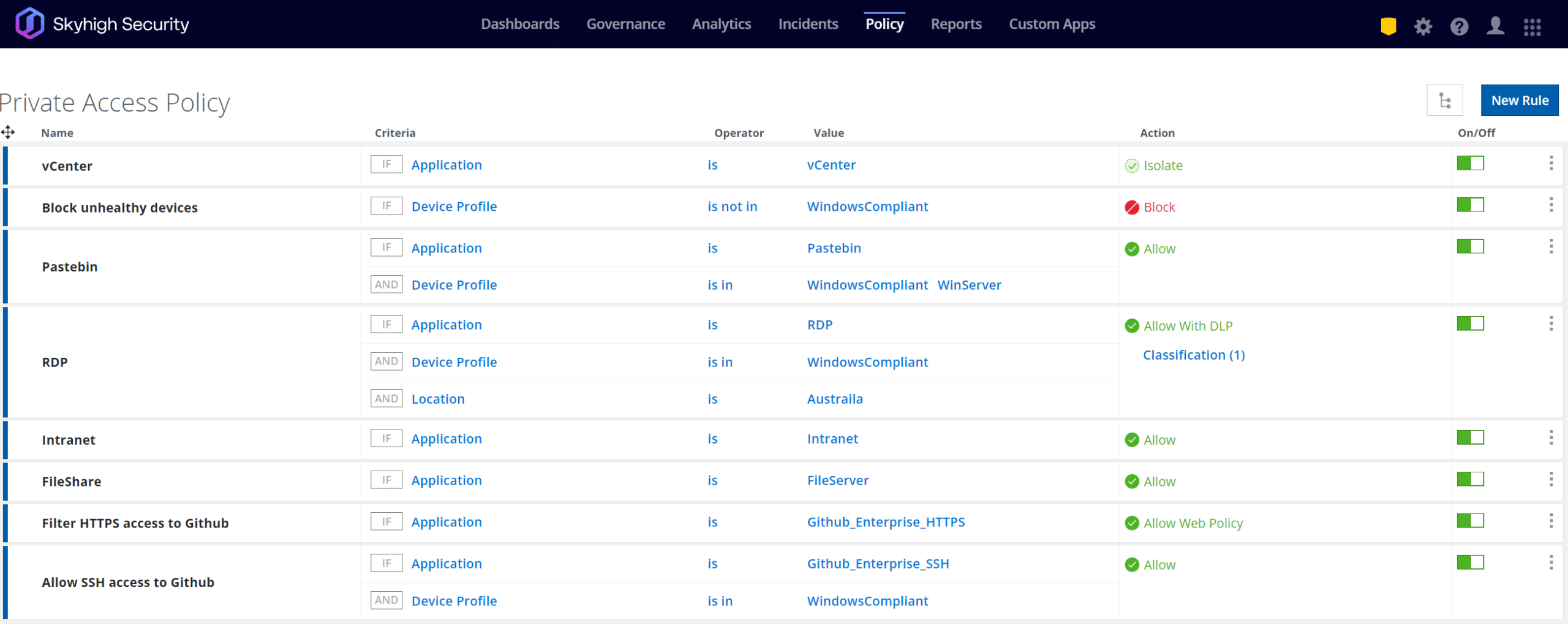 Figure 3. Skyhigh Security: Segment private networks and apps with Zero Trust direct-to-app connections
Figure 3. Skyhigh Security: Segment private networks and apps with Zero Trust direct-to-app connections
Network segmentation is another essential security control that organizations should utilize, as it provides enhanced protection for high-value assets and helps prevent lateral movements and data exfiltration attempts in situations where an adversary is able to gain initial access into the environment.
To help with adopting this guidance, organizations should avoid have one single, pipe in and out of their network. In a Zero Trust architecture, networks are instead segmented into smaller fragments where specific workloads are contained. Each fragment can have its own ingress and egress controls, posture checks, contextual access controls, data protections, and much more to minimize the “blast radius” of unauthorized access.
With a Zero Trust methodology, you increase the difficulty for unauthorized actors to propagate throughout your networks, thereby reducing the lateral movement of threats.
As data continues to be spread across our cloud infrastructures to enable productivity, ensure you not only enable content-aware collaboration controls between cloud apps, but also implement cloud Data Loss Prevention capabilities to avoid sacrificing security at the hands of a simple, compromised VPN session.