Resources
INTELLIGENCE DIGEST
Ransomware’s Evolution
Attacks shift focus from file encryption to data exfiltration for extortion
By Rodman Ramezanian - Global Cloud Threat Lead
June 30, 2023 7 Minute Read
A recent advisory jointly released by the Federal Bureau of Investigation (FBI), Cybersecurity and Infrastructure Security Agency (CISA), and Australian Cyber Security Centre (ACSC) details the heightened threats posed by the BianLian ransomware and extortion group. With the cybercriminal group active since June 2022, it appears that the more conventional encryption of victim files for ransomware payouts has now been shifted to exfiltration of compromised data for blackmail and extortion purposes.
Typically gaining access via valid Remote Desktop Protocol (RDP) credentials, BianLian’s ransomware campaign has targeted well-known organizations across education, healthcare, critical infrastructure, banking, financial services and insurance, media and entertainment, manufacturing, and other verticals.
According to the advisory, “BianLian group engages in additional techniques to pressure the victim into paying the ransom; for example, printing the ransom note to printers on the compromised network. Employees of victim companies also reported receiving threatening telephone calls from individuals associated with the BianLian group.”
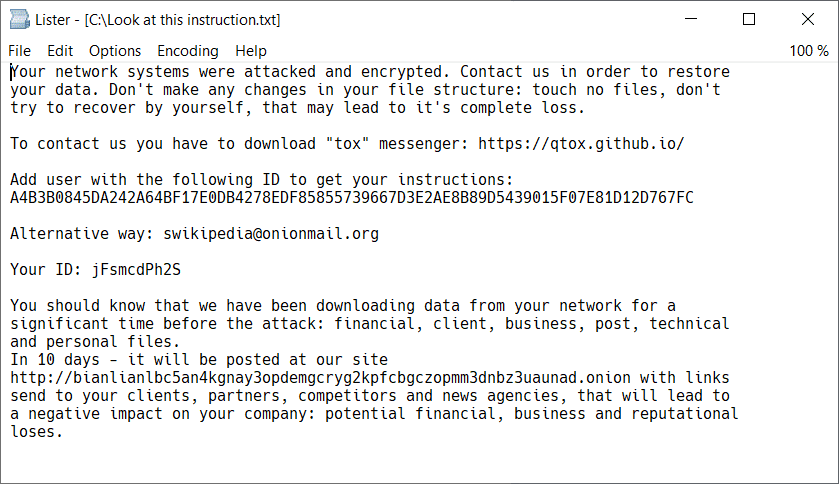
Among many cautions and recommendations offered by the respective intelligence agencies, the advisory outlines the importance of organizations “… strictly limiting the use of RDP and other remote desktop services …” to reduce attack surfaces and deny opportunities for unauthorized lateral movements. This is particularly important because the BianLian group, unlike most other ransomware groups, relies primarily on technical exploitation of remote access tools rather than the more orthodox Tactics, Techniques, and Procedures (TTPs) solely dependent on unsolicited phishing emails.
With a stronger focus on data exfiltration, this latest iteration of BianLian’s ransomware strain “uses File Transfer Protocol and Rclone, a tool used to sync files to cloud storage in order to exfiltrate data. FBI observed that the BianLian group actors install Rclone and other files in generic and typically unchecked folders … ACSC observed BianLian group actors use Mega file-sharing service to exfiltrate victim data.”
Why do these incidents occur?
Today, ransomware as its own threat vector wouldn’t exactly be considered “novel.” Where there’s data, there’s an opening for threat actors to hold this sensitive information hostage and demand payment for its release. This concept stems back to the early days of malware infections, when the “AIDS virus” strain came on the scene as one of the first instances of ransomware.
The extortion and data theft approach continues to rise in popularity among ransomware groups, as victim organizations are taking a stricter stance on giving into traditional ransomware payment demands. With this revamped “modus operandi,” the threat actors gain their initial access, move laterally throughout the victim’s networks, find sensitive/valuable data for subsequent exfiltration, deploy their ransomware payloads, and ultimately issue their demands. From that point, if the victim organization doesn’t pay the initial ransom demand, the threat actors will threaten to leak stolen data online.
Unfortunately, this new-and-improved double extortion model is gaining stronger traction among cybercriminals and their threat campaigns, wherein they demand separate payments for decrypting the affected systems and for not leaking the victim’s stolen data.
What can be done?
As a bare minimum, foundational security guidelines and multifactor authentication should be enabled and used wherever possible. This is specifically called out in the aforementioned advisory as “phishing-resistant multifactor authentication.” BianLian serves as yet another example of how static, valid credentials are being obtained and exploited to facilitate greater access into a victim’s infrastructure.
Ransomware, as the name suggests, primarily focuses on holding a victim organization’s data hostage for ransom (no points for guessing that one). How? Traditionally, this is done by encrypting a victim’s files. If your organization’s files have been taken hostage using the threat group’s encryption algorithms, the team at Avast has developed a BianLian-specific decryption tool to help victims retrieve their encrypted data for free and avoid paying ransom to the attackers.
Additionally, organizations are strongly encouraged to leverage known Indicators of Compromise (IOC) in their appropriate platforms to detect, remediate, and prevent BianLian infections.
As pointed out by the respective intelligence agencies in their advisory, attack surface reduction is an important risk mitigation technique to be considered, particularly when lateral movements appear to be another common TTP here. Strictly limiting RDP and remote desktop services is a common recommendation offered for recent threats such as Lapsus$ and Venus, and is one that should be taken equally seriously for BianLian.
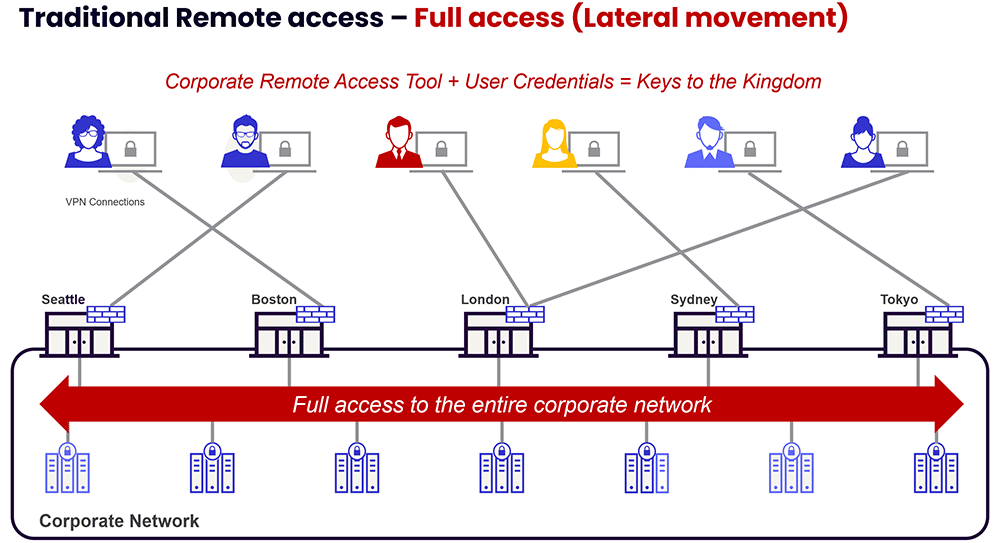
Understandably, today’s organizations rely heavily on remote access services and capabilities to allow their workforces to function and collaborate across distributed settings. For this reason, taking a heavy-handed approach by simply “doing away” with existing RDP tools may not be feasible. Instead, organizations should find ways to mitigate the underlying risks associated with remote desktop use and exploitation wherever possible.
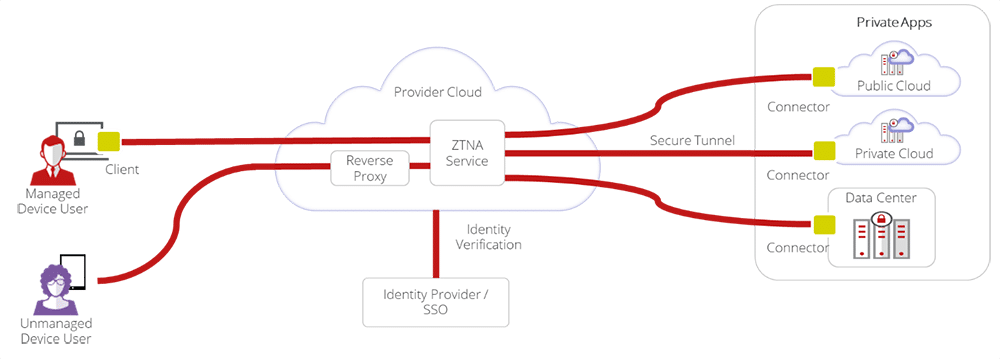
As an example, aligning to principles of Zero Trust Network Access (ZTNA) can greatly assist with attack surface reduction—meaning that access to any resource is denied by default. Every user and device, whether internal or remote, is assumed to be unsecure and risky, and their identity and security posture must be verified before granting access to sensitive private resources, including RDP connectivity services.
ZTNA allows organizations to create software-defined perimeters and divide the corporate network into multiple micro-segments. By only allowing “least privilege” access to specific applications and internal resources—not the entire underlying network to any user with valid login keys—the attack surface is dramatically reduced, thereby preventing lateral movement of threats from compromised accounts or devices.
References:
- https://www.cisa.gov/news-events/cybersecurity-advisories/aa23-136a
- https://www.cisa.gov/sites/default/files/publications/fact-sheet-implementing-phishing-resistant-mfa-508c.pdf
- https://decoded.avast.io/threatresearch/decrypted-bianlian-ransomware/
- https://www.bleepingcomputer.com/news/security/venus-ransomware-targets-publicly-exposed-remote-desktop-services/
Use Skyhigh Security?
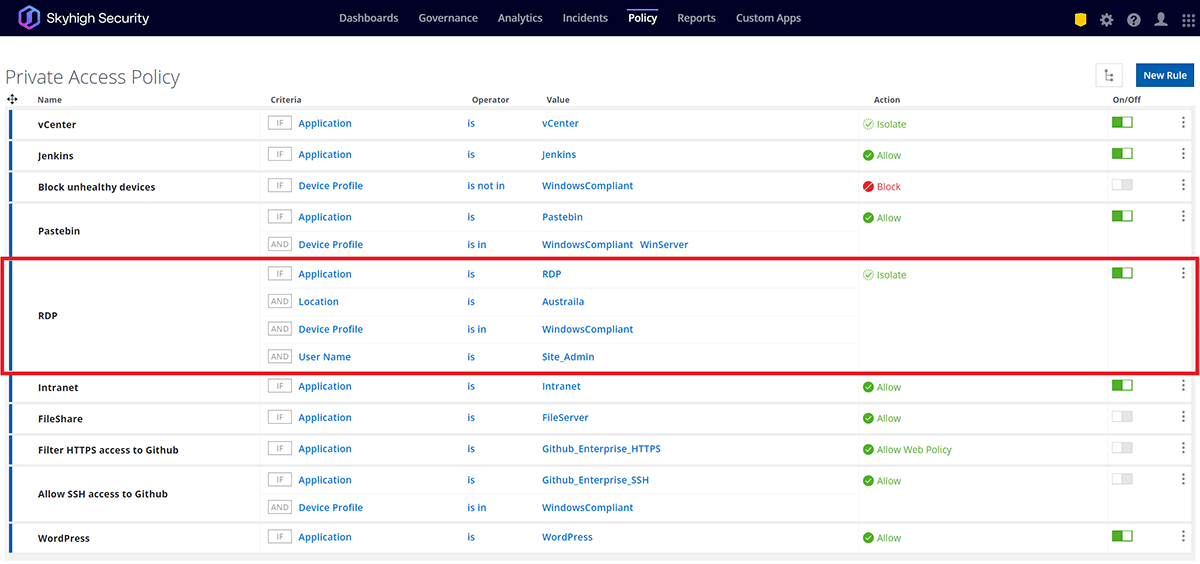
- Leverage Private Access policy rules to enforce controlled access directly to private applications, eliminating risks of lateral movement.
- Define Device Profiles and Posture Assessments for managed/unmanaged devices requesting access to corporate resources, either internally or externally.
- Enable configuration audits to discover and monitor services exposed to unrestricted access.
- Evaluate user activities beyond initial logins to include user movements, behaviors, access to corporate services, locations, and many other potential anomalies.
- Block unmanaged devices, enforce multifactor authentication and many other contextual access policies to help stop the successful reuse of stolen cloud application credentials.
With over 11 years’ worth of extensive cybersecurity industry experience, Rodman Ramezanian is an Enterprise Cloud Security Advisor, responsible for Technical Advisory, Enablement, Solution Design and Architecture at Skyhigh Security. In this role, Rodman primarily focuses on Australian Federal Government, Defense, and Enterprise organizations.
Rodman specializes in the areas of Adversarial Threat Intelligence, Cyber Crime, Data Protection, and Cloud Security. He is an Australian Signals Directorate (ASD)-endorsed IRAP Assessor – currently holding CISSP, CCSP, CISA, CDPSE, Microsoft Azure, and MITRE ATT&CK CTI certifications.
Candidly, Rodman has a strong passion for articulating complex matters in simple terms, helping the average person and new security professionals understand the what, why, and how of cybersecurity.
Attack Highlights
- BianLian threat actors gain initial access to victim networks by leveraging valid, compromised Remote Desktop Protocol (RDP) credentials acquired from external initial access brokers or via phishing techniques.
- Following successful exploitation, the operators prepare for remote execution of system commands by deploying malicious web shell scripts on infected systems.
- BianLian group actors implant a custom backdoor specific to each victim and install remote management and access software—such as TeamViewer, Atera Agent, SplashTop, AnyDesk—for persistence and command and control.
- The threat actors then use valid accounts for lateral movement through the network and to pursue other follow-on activities.
- To ultimately exfiltrate data for extortion purposes, the group uses a combination of File Transfer Protocol (FTP) and Rclone, a file synchronization tool directed at cloud storage infrastructure.









