By Hari Prasad Mariswamy - Product Management, Skyhigh Security
November 21, 2022 3 Minute Read

Research shows that modern day organizations invest more into protecting the most sensitive data from being exfiltrated into unsanctioned applications, users and devices. Whilst there are many ways in which data loss prevention (DLP) administrators can configure policies to safeguard this data, there are still data leakages we keep hearing about. This can be dreadful to financial, or healthcare based organizations who strive on protecting their customer’s private data thereby risking compliance with standard regulations such as GDPR, HIPPA etc.
Choosing the right DLP solution
Some of the common approaches to defining DLP rules include building a large dictionary of keywords or terms, crafting complex regular expressions to match all data types related to sensitive personally identifiable information (PII)These techniques are effective in places where there are standard data types such as a list of IP addresses or an ISO standard for data formats where regular expressions can be applied. They do not fit the purpose when enterprises are looking to prevent their customer records or sensitive PII information from being lost as there can be new forms/formats of data that will evade these policies causing data leakage. For instance, a financial organization’s customer PII data can be stored in a database as records in row and column format and this needs to be protected from being exfiltrated to prevent potential data leakages. Exact Data Matching (EDM) is a technique of DLP that can play a crucial role in such scenarios.
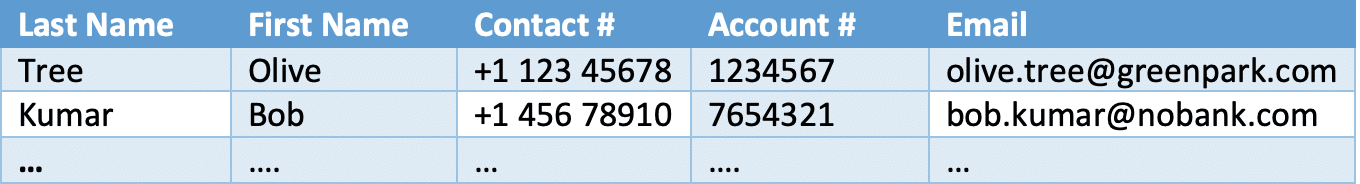
How does Skyhigh’s EDM work
EDM works by fingerprinting large amounts of structured data organized as rows and columns. Skyhigh Security’s DLP integrator tool, once installed on a customer’s on-premises local server, is used to fingerprint these large data stores with billions of cells and upload the trained fingerprints securely to the Cloud DLP with innovative industry-leading fingerprinting techniques. This helps to deploy Data Protection rules faster with these large fingerprint datasets efficiently to protect the most sensitive data in its exact form. For instance, Skyhigh Security’s fingerprint tool can train a database table consisting of data in “any language” and spread across about 6 billion cells in approximately six hours, which is significantly faster in comparison to some of the other leading vendors.
Also called Structured Fingerprints, EDM Fingerprints can then be used as a content match criterion in data classifications, which then aid in preventing data exfiltration where the fingerprints are matched precisely. With its exact matching capabilities, it not only takes away the manual burden on DLP administrators to carefully craft a complex regular expression, but also provides the highest level of compliance adherence for enterprises.
A true unified EDM solution
With Skyhigh’s truly multi-vector Data Protection solution for Security Service Edge (SSE), the Unified EDM structured fingerprints trained once (manually via the DLP integrator tool or via scheduled API automation) can be used as part of “Common Classifications” for DLP policies to protect data exfiltrated across various vectors, including:
- High-Risk cloud services
- Permitted cloud services
- Sanctioned cloud services
- Email
- Private applications
- On-premises network traffic
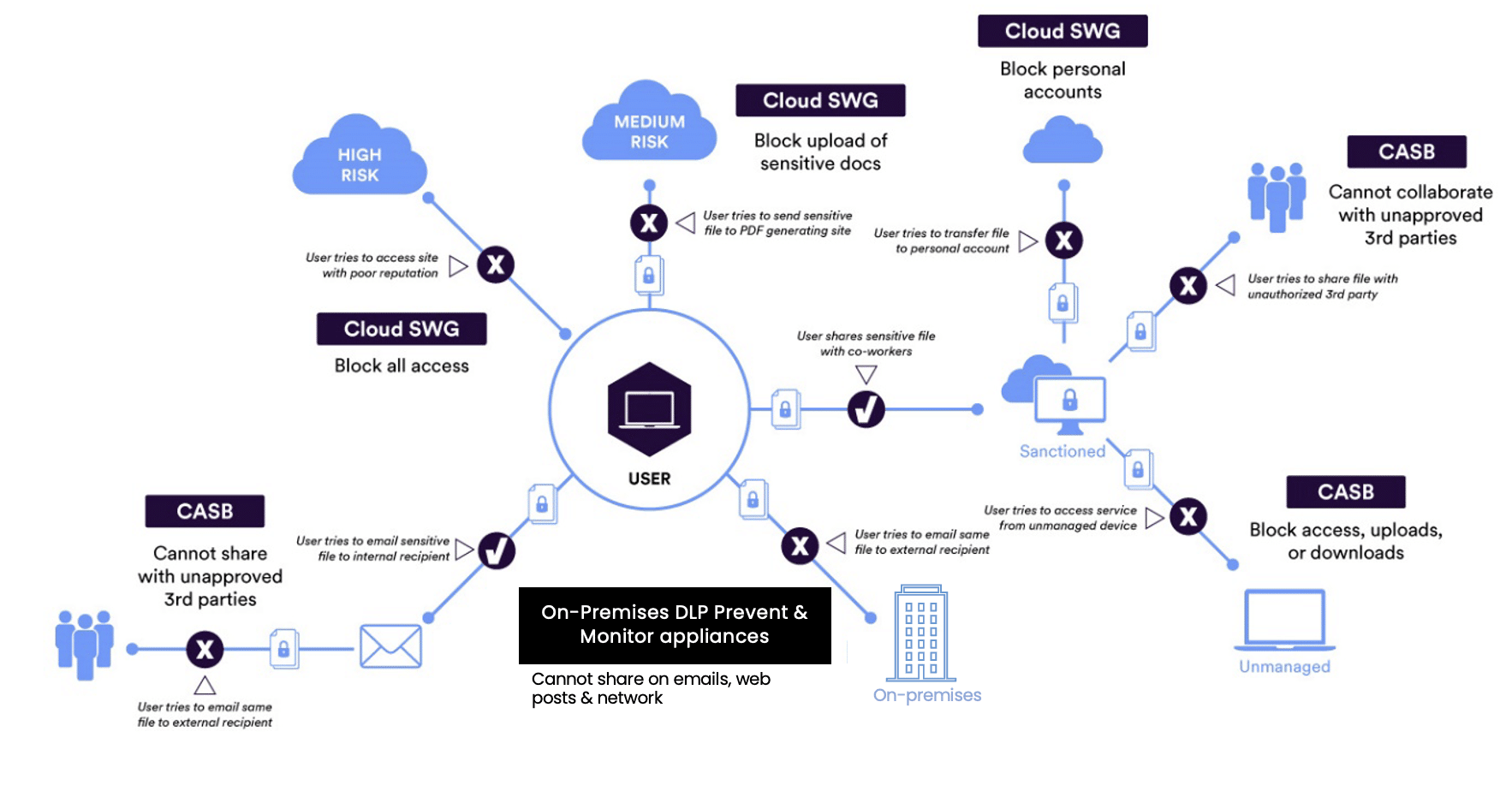
To provide data protection across all the exfiltration vectors, DLP protection works consistently across all the deployment modes for SSE, including Forward Proxy, API, Reverse Proxy, and SMTP.
While protecting data in real-time is critical, it is equally important for enterprises to realize where their sensitive data is stored and who has access to it. Skyhigh Security’s DLP On-Demand Scan (ODS) allows organizations to schedule and run DLP scans for data at rest on cloud services, enterprise email mailboxes, and on-premises network shares. ODS scans are empowered to use structured fingerprints to discover sensitive data and classify it with appropriate labels.

Finally, Skyhigh Security’s unified incident management console acts as a single pane of glass to help DLP administrators easily manage all data-related violations across sanctioned and Shadow IT applications. Incidents related to EDM violations for both sanctioned and Shadow-IT applications provide detailed analytics by showing match highlights as extracts from documents.
Click here to get started with Skyhigh Security’s Unified Exact Data Matching capability for Data Protection, learn how to create fingerprints and automate the process for any database changes.
Back to Blogs