Resources
INTELLIGENCE DIGEST
It’s Plane To See – Unsecured Servers Can Put Lives at Stake
How An Exposed Amazon S3 Bucket Exposed 3TB Worth Of Sensitive Airport Data
By Rodman Ramezanian - Enterprise Cloud Security Advisor
July 6, 2022 7 Minute Read
An unsecured server has exposed sensitive data belonging to airport employees across Colombia and Peru. The AWS S3 buckets containing approximately 3TB of data dating back to 2018 consisted of airport employee records, ID card photos, and personally identifiable information (PII), including names, photos, occupations, and national ID numbers.
Airport security protects the lives of travelers and airport staff. As such, this breach, which was discovered by SafetyDetectives, is extremely dangerous with potentially devastating consequences should the bucket’s content end up in the wrong hands. Within Colombia, Peru, and around the world, guerrilla criminals and terrorist organizations now pose a serious threat if they were to access this unsecured AWS S3 bucket.
Sadly, such types of breaches and incidents are not novel or unique as organizations stumble in the cloud.
Part of the problem is the unanticipated speed with which many organizations have undertaken their cloud adoption process, in a desperate scramble to provision their employees to work remotely as a result of the COVID-19 pandemic. As expected, threat actors and APT groups, relish these prospects.
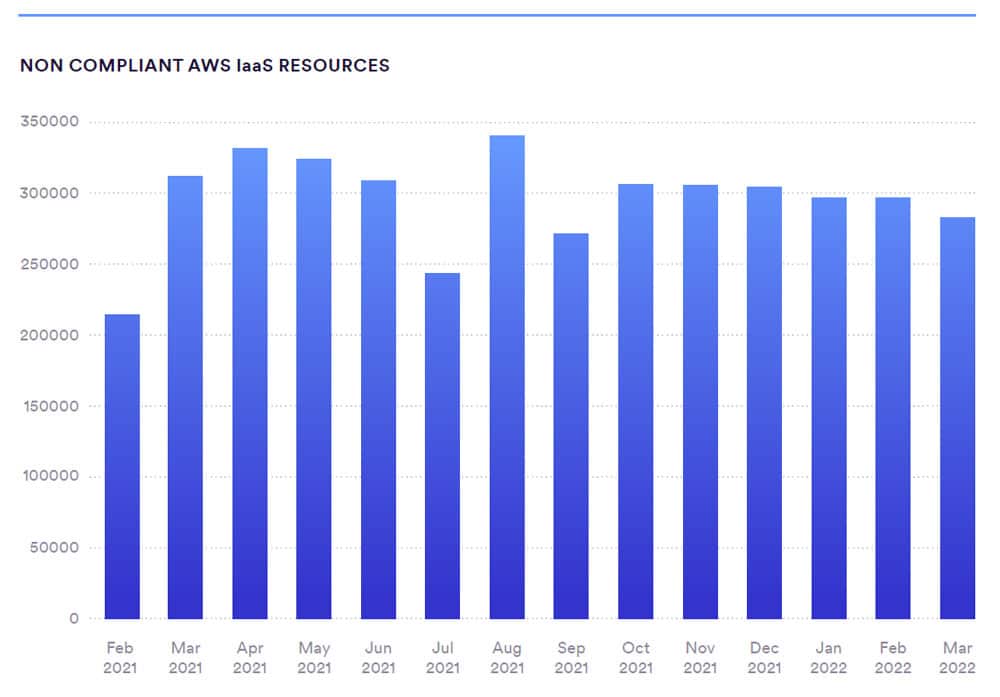
How did these breaches occur?
Most organizations that fail to control public cloud use will inappropriately share sensitive data. Unfortunately, news headlines like these highlight examples of a data breach due to a simple, but harmful misconfiguration: an unsecured, exposed cloud storage service. Complexities around identity management, access permissions, secure configurations, data protection, and so much more, continuously result in poor cloud security hygiene and ultimately, data exposures.
What can be done?
Ideally, tightening read/write permissions may be the first and only reactions that come to mind. In reality, it will take far more than that; thanks to the extensive manners by which cloud storages can be accessed and misused. Skyhigh Security addresses these challenges and minimizes associated risks by applying a number of fundamental capabilities, thanks to tight integrations into many cloud platforms.
As global breaches continue to arise at the hands of ransomware attacks and criminal actors, Skyhigh Security’s cloud security posture management, vulnerability assessments, configuration audits, and data protection capabilities aid organizations by continuously applying optimal security while reducing complexities related to managing storage across multi-cloud environments.
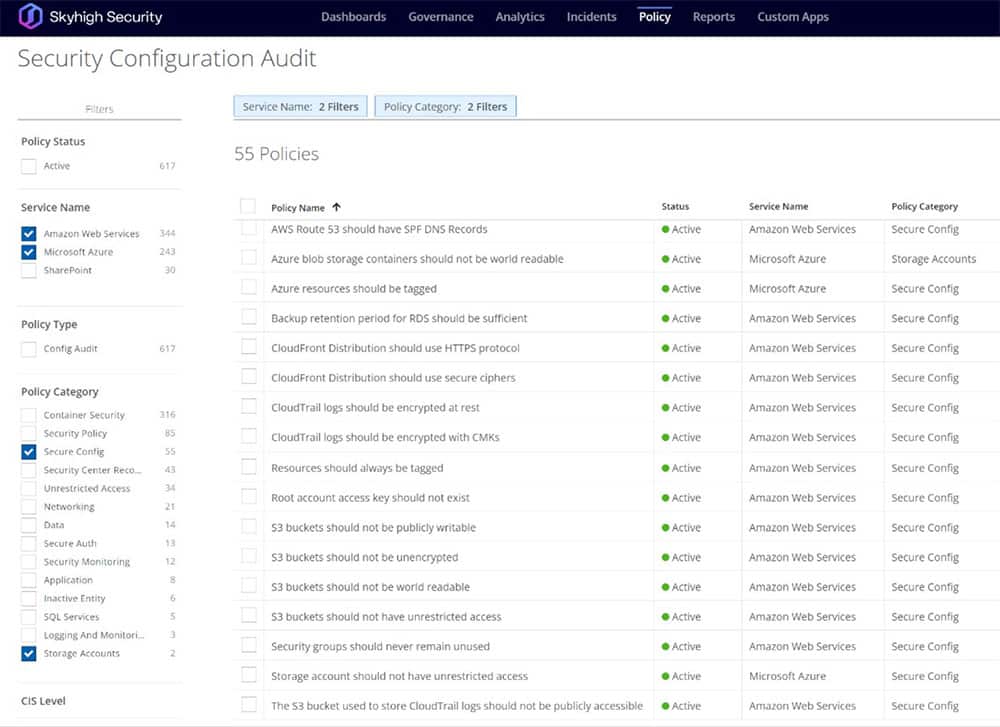
Use Skyhigh Security?
- Enable automatic scanning for vulnerable storage across AWS S3 Buckets and Azure Blobs
- Use continuous configuration audits for IaaS Accounts and Services to enforce consistent protection
- Enforce compliance checks against industry best practices to maintain secure postures
- Run data loss prevention and malware scans to detect violations in cloud storage services and protect sensitive data from being exfiltrated
- Detect insider threats as well as threats from compromised accounts and privileged access misuse
- Apply automatic remediations to take appropriate action against misconfigurations, vulnerabilities, and exposures
With over 11 years’ worth of extensive cybersecurity industry experience, Rodman Ramezanian is an Enterprise Cloud Security Advisor, responsible for Technical Advisory, Enablement, Solution Design and Architecture at Skyhigh Security. In this role, Rodman primarily focuses on Australian Federal Government, Defense, and Enterprise organizations.
Rodman specializes in the areas of Adversarial Threat Intelligence, Cyber Crime, Data Protection, and Cloud Security. He is an Australian Signals Directorate (ASD)-endorsed IRAP Assessor – currently holding CISSP, CCSP, CISA, CDPSE, Microsoft Azure, and MITRE ATT&CK CTI certifications.
Candidly, Rodman has a strong passion for articulating complex matters in simple terms, helping the average person and new security professionals understand the what, why, and how of cybersecurity.
Attack Highlights
- Security service provider misconfigures AWS S3 bucket containing ~1.5 million files (3TB)
- Unsecured bucket was publicly accessible, open, did not require authentication for access
- Exposed information included employee PII and sensitive company data of at least four airports in Colombia and Peru
- Data also included photos of airline employees, planes, fuel lines, national ID cards, GPS map coordinates, and luggage
- Android mobile apps contained within buckets, used by security personnel to help with incident reporting and data handling
- Leaked airport photo ID cards present grave threats from terrorist organisations and criminal groups









