Resources
INTELLIGENCE DIGEST
Double Trouble: Midnight Blizzard Rattles Microsoft and HPE in Hacking Fiasco
Both organizations fall victim to attacks waged by state-sponsored actors behind SolarWinds incident
By Rodman Ramezanian - Enterprise Cloud Security Advisor
February 26, 2024 7 Minute Read
Recent reports of both Microsoft and Hewlett Packard Enterprise (HPE) being breached via their cloud-based email infrastructures have taken the cybersecurity industry by storm; frankly, for more reasons than one! For those who recall the SolarWinds hacks back in 2020, it appears the same actors, now more commonly referred to as Midnight Blizzard (aka Cozy Bear, Nobelium, APT29) appear to be at it again.
Although the breaches of both HPE and Microsoft were disclosed within days of each other, the situation predominantly underscores the ongoing reality of Midnight Blizzard’s international espionage endeavors—with reports strongly linking the threat group to the Russian Foreign Intelligence Service (SVR) and its persistence in exploiting vulnerabilities within organizations’ digital footprints and assets.
There was consistency across both incidents in that the Midnight Blizzard operators gained access to HPE and Microsoft’s cloud-based email environments, via targeting of individual employee mailboxes, and password spray attacks, respectively.
HPE stated that the hacking group “accessed and exfiltrated data” from a “limited number” of HPE’s 365 mailboxes after gaining access via compromised accounts.
In the case of Microsoft, the attackers utilized their initial access to identify and infiltrate a legacy test OAuth application with elevated access to the Microsoft corporate environment. Exploiting this application enabled them to generate even more malicious OAuth applications, eventually allowing them to grant themselves privileged Microsoft 365 Exchange Online roles. This tactic allowed them to gain access to mailboxes within the system.
To compound the threat, the group has been observed employing session replay attacks, enabling them to gain initial access to cloud resources by leveraging stolen sessions acquired through illicit methods and access brokers.
Considering Microsoft’s previous research and public posts warning about threat actors exploiting OAuth applications within victims’ networks, these attacks are intriguing just as they are eyebrow-raising. In a blog post from Microsoft back in 2022, the company outlined an attack where threat actors employed credential stuffing against an organization’s cloud tenant accounts lacking multi-factor authentication (MFA) protection. Subsequently, the threat actor used the access to cloud tenant accounts to create malicious OAuth apps, providing them entry into the victim’s Exchange Online instance. Ironically, this wasn’t far at all from what transpired against Microsoft in this instance.
Why do these incidents occur?
Analyzing the activities of Midnight Blizzard reveals the group’s sophistication, as they employ a blend of custom-designed malware and altered publicly accessible tools to bypass authentication mechanisms, infiltrate their targets, and elude detection.
Although Microsoft is frequently targeted due to its significant size and influence in IT infrastructure, there has been a recent surge in successful attacks on both their products and internal systems. Incidents like the one here utilizing password-spraying could have been mitigated with multi-factor authentication—a measure that was evidently not implemented. Microsoft advocates for MFA as a crucial component of robust cyber hygiene. Given their position in the security ecosystem, it is imperative to hold them to a higher level of accountability.
In Microsoft’s own words, “the attack was not the result of a vulnerability in Microsoft products or services” and this is important in the context of understanding why this incident occurred. Unfortunately for Microsoft, it came down to how poorly their cloud environments and infrastructures were configured for protection.
Falling victim to Microsoft 365 email account takeover attacks are not new, and this is a great example of how even industry behemoths like HPE can be targeted and infiltrated successfully from the cloud vector.
The harsh reality is that it’s hardly surprising to see large, multinational IT organizations being targeted nowadays; particularly when it involves exfiltration and theft of data as was the case in both of these incidents. The more alarming trend, however, is how often these organizations are being targeted via their cloud environments and assets.
The same way that cloud computing invites scalability, flexibility, growth, and collaboration for companies of all shapes and sizes, it also entices cybercriminals—particularly the highly skilled and motivated state-sponsored actors—to look for opportunities (and there are many of them) where federated access tokens can be swiped, cloud assets may be misconfigured and vulnerable, or email users can be swayed with some clever social engineering techniques. Thanks to the interconnected nature of cloud environments and platforms, being successful in even just one of these efforts can be enough for attackers to get to work.
What can be done?
These incidents should act as sobering reminders to organizations of every size and across all sectors: cyberattacks can target anyone, regardless of their stature, even industry giants. The truth is that every enterprise platform, infrastructure element, and supporting technology is a prime target for potential attacks.
There are, however, fundamental, nonnegotiable security features and processes that need to be enabled and adopted to defend valuable assets, or at least make the jobs of attackers harder. Things like:
- Enforcing MFA everywhere possible
- Auditing OAuth applications and tokens, with the ability to revoke at any time (especially those known to be “legacy”)
- Managing security posture (because there’s always bound to be something missed or overlooked)
- Monitoring anomalies to detect suspicious account behaviors (such as creation of new applications, assigning of new/privileged roles, exfiltration of data)
Allow me to elaborate:
Configuration audits and posture assessments can identify and help rectify misconfigurations where MFA may not have been enforced, say at the root Azure Security Center level (figure 1).
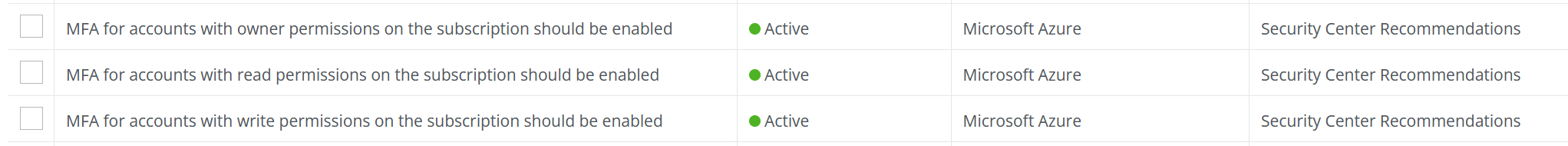
The attackers leveraged a malicious OAuth application to help broker access and elevate privileges to a point where they could jump across to the corporate Microsoft tenant that housed their executives’ emails. Security teams must be able to “remediate, audit, allow, or block Connected OAuth apps” that have access to user data.
Maintaining app governance and control over how they can interact with corporate data within M365 is critical (figure 2).
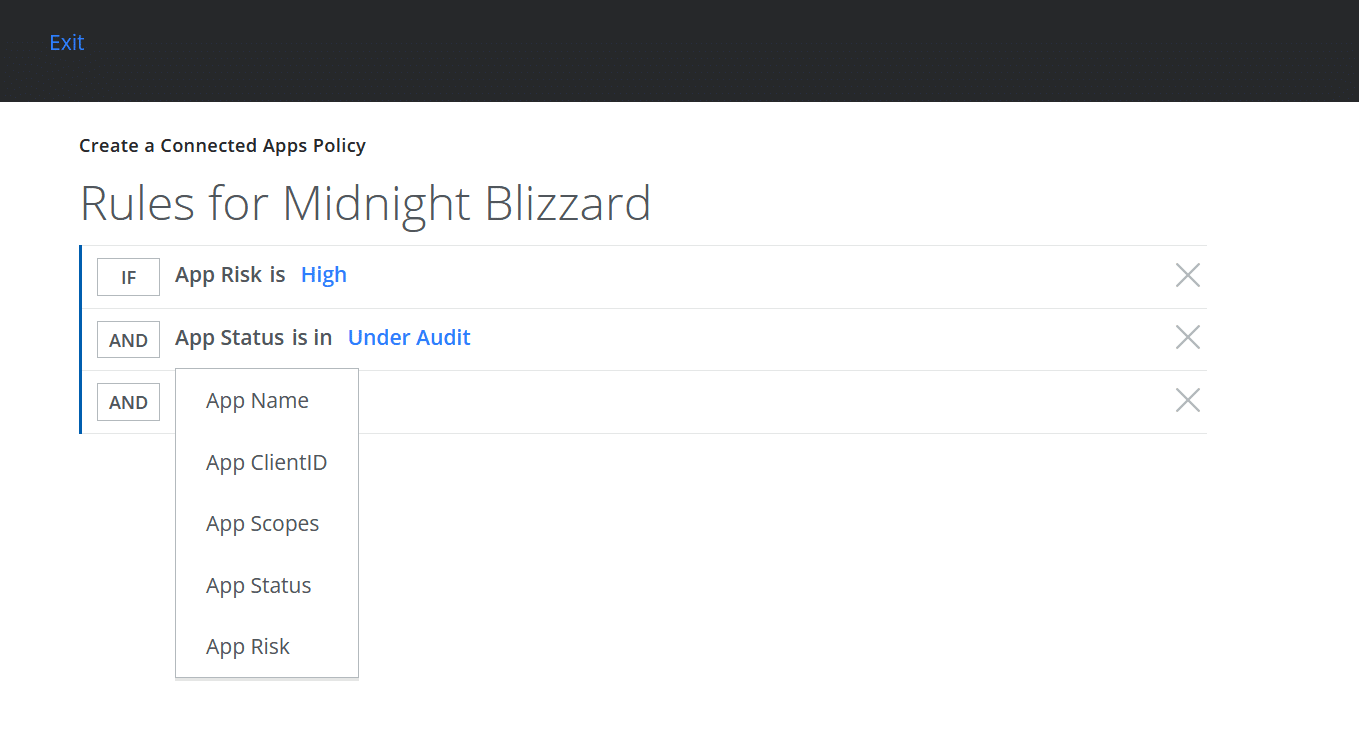
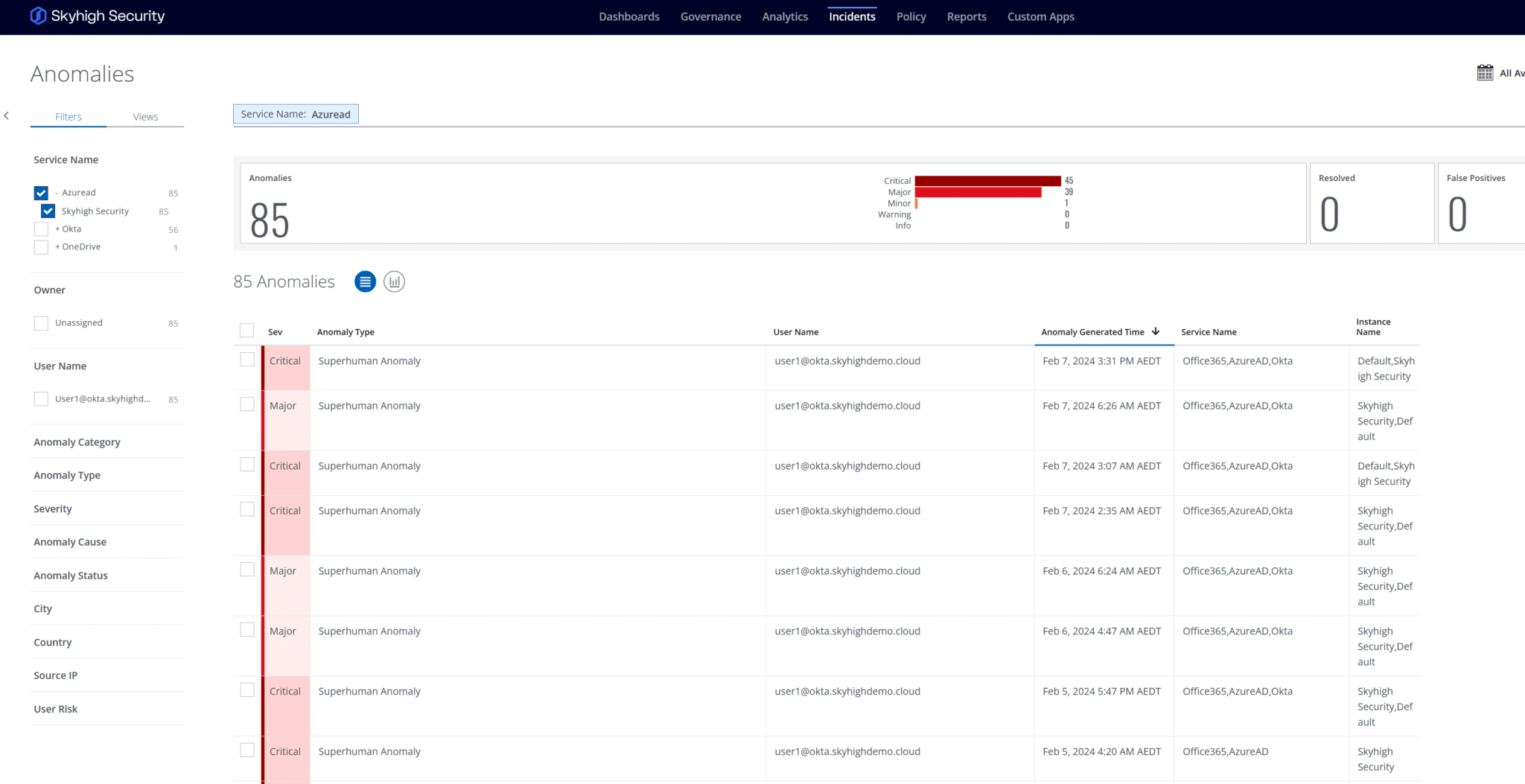
Regarding identity (Entra ID) and M365 behaviors, security teams need the ability to detect, highlight, and prevent anomalies and suspicious behaviors across their Microsoft 365 environments, as well as their security roles and permissions.
References:
- https://www.bleepingcomputer.com/news/security/hpe-russian-hackers-breached-its-security-teams-email-accounts/
- https://securityaffairs.com/157802/apt/midnight-blizzard-hacked-microsoft-email-accounts.html
- https://thehackernews.com/2024/01/microsoft-warns-of-widening-apt29.html
- https://www.wired.com/story/microsoft-hpe-midnight-blizzard-email-breaches/
Use Skyhigh Security?
- Perform security audits on cloud environments where MFA isn’t enabled and enforced.
- Maintain app governance and control over how connected apps can interact with corporate data within M365.
- Extend data loss prevention to Exchange Online mailboxes to prevent data exfiltration (in the event of account takeover).
- Define acceptable administrative behaviors to detect anomalies involving privileged access misuse.
- Monitor and baseline user activities to help highlight suspicious outliers.
- Align threats, anomalies, and incidents to the MITRE ATT&CK framework to guide SOC analysts for investigations.
With over 11 years’ worth of extensive cybersecurity industry experience, Rodman Ramezanian is an Enterprise Cloud Security Advisor, responsible for Technical Advisory, Enablement, Solution Design and Architecture at Skyhigh Security. In this role, Rodman primarily focuses on Australian Federal Government, Defense, and Enterprise organizations.
Rodman specializes in the areas of Adversarial Threat Intelligence, Cyber Crime, Data Protection, and Cloud Security. He is an Australian Signals Directorate (ASD)-endorsed IRAP Assessor – currently holding CISSP, CCSP, CISA, CDPSE, Microsoft Azure, and MITRE ATT&CK CTI certifications.
Candidly, Rodman has a strong passion for articulating complex matters in simple terms, helping the average person and new security professionals understand the what, why, and how of cybersecurity.
Attack Highlights
- Hewlett Packard Enterprise (HPE) revealed that a group of suspected Russian hackers, identified as Midnight Blizzard, infiltrated the company’s Microsoft 365 email system to extract data from its cybersecurity team and other departments.
- Preliminary findings from HPE suggest a potential connection to a prior incident in May 2023, during which the threat actors reportedly infiltrated the company’s SharePoint server and extracted files.
- During the November 2023 incident aimed at Microsoft, the threat actor used a password spray attack to effectively penetrate a legacy, non-production test tenant account lacking MFA. This granted the attackers a valuable foothold.
- The attackers proceeded to use their initial access to identify and infiltrate a legacy test OAuth application with elevated access to the Microsoft corporate environment.
- This legacy application was weaponized to create additional malicious OAuth applications, granting them the Microsoft 365 Exchange Online full access role, thereby gaining access to Microsoft’s mailboxes.
- Subsequently, the threat group used the account’s privileges to access a select portion of Microsoft corporate email accounts, encompassing members of Microsoft’s senior leadership team, as well as employees in their cybersecurity, legal, and other departments. This allowed the Midnight Blizzard operators to extract some emails and attached documents.
- According to Microsoft, the attack did not occur due to a vulnerability in Microsoft products and services.









