Resources
INTELLIGENCE DIGEST
MGM Resorts cyberattack–from cloud to casino floor
Widespread disruption at the hands of stinging social engineering and ransomware attacks
By Rodman Ramezanian - Global Cloud Threat Lead
October 18, 2023 7 Minute Read
The recent cyber intrusion targeting MGM Resorts International has underscored pressing issues surrounding the safeguarding of sensitive data and the exposed vulnerabilities that modern organizations confront within today’s threat landscape.
MGM Resorts, the operator of several renowned hotels and casinos along the iconic Las Vegas Strip, including the Bellagio, Aria, and Cosmopolitan, initiated extensive network shutdowns in response to intensifying cyberattacks. This led to significant disruptions throughout its hotel and casino properties, with guests experiencing issues ranging from unavailable ATMs and slot machines to malfunctioning room digital key cards and electronic payment systems.
The culprits? Cybercriminals with a knack for social engineering. They’ve gained recognition in cybersecurity circles for a unique trait—their fluent proficiency with the English language, setting them apart from the majority of cybercrime groups whose English skills typically fall short.
Interestingly, thanks to their comparable tactics, techniques, and procedures (TTPs), researchers at Mandiant have detected a correlation between Scattered Spider and the Lapsus$ hacking group, which share similar team compositions and approaches (see Figure 1).¹
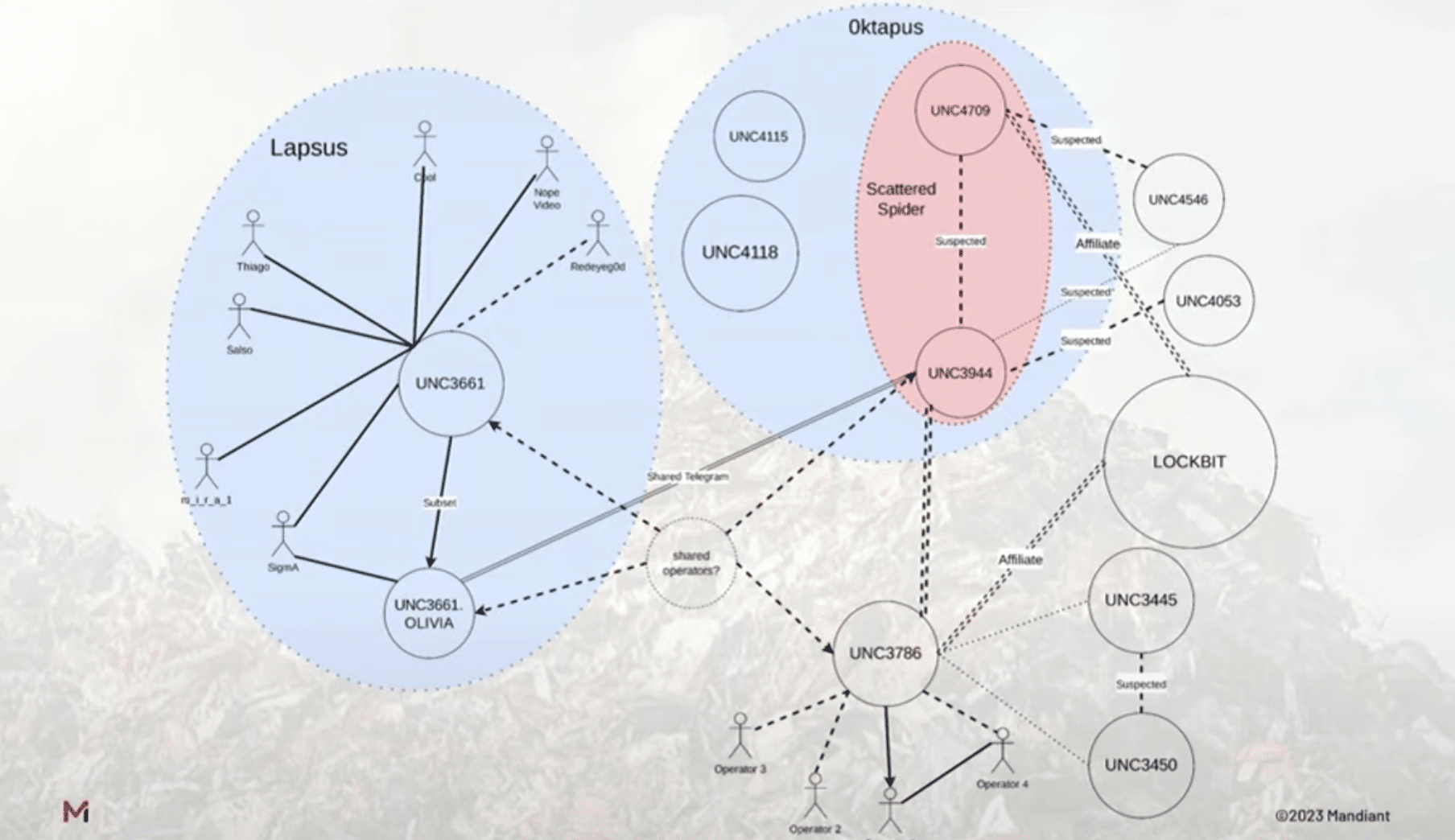
Their tradecraft? A cleverly executed social engineering maneuver paved their way to initial access, utilizing an senior MGM user’s LinkedIn profile to facilitate the resetting of multifactor authentication (MFA) requests via the internal helpdesk.
According to numerous security reports on the matter, the perpetrators established persistence within MGM’s network by setting up an additional Identity Provider (IdP) in their Okta tenant using a feature known as “inbound federation.” While this is typically used for quick connections and integrations during organizational mergers and acquisitions, in this instance, the threat actors exploited it to enhance their hold over the victim’s networks.
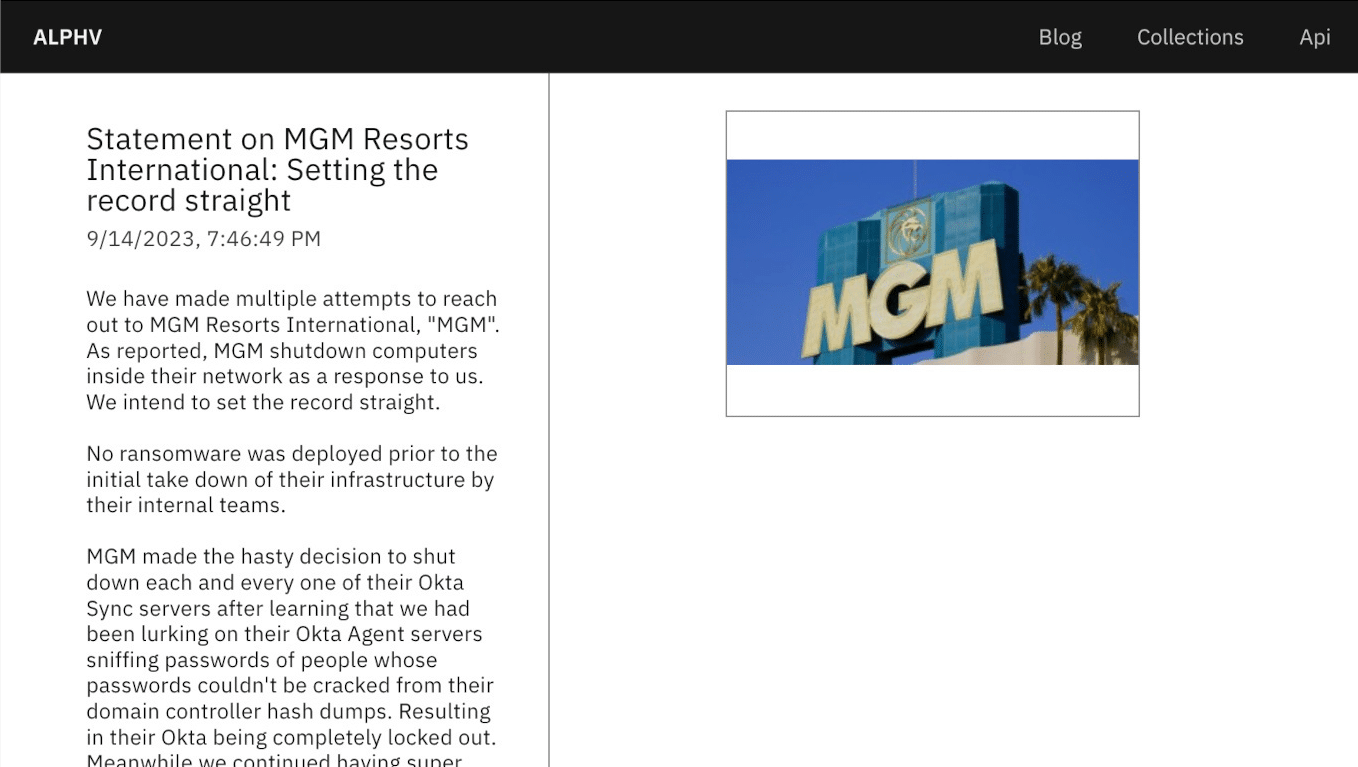
From that point, the attackers took charge of MGM’s Okta and the Microsoft Azure cloud environments, commandeering not only the identity and access management (IAM) platform-managed applications but also their cloud assets. Even after MGM cybersecurity personnel shut down Okta server synchronization, the hackers remained within the network, as confirmed in their statement (see Figure 2).² They asserted having retained super administrator privileges on MGM’s Okta environment and Global Administrator permissions for MGM’s Microsoft Azure tenant.
Ultimately, they encrypted hundreds of ESXi servers, housing thousands of VMs that supported numerous hospitality systems, triggering widespread havoc. As the ESXi hosts were encrypted sequentially, applications crashed in succession. This led to inoperable slot machines, dysfunctional hotel room keys, disrupted dinner reservations, non-operational point-of-sale systems, and guests being unable to check in or out.
Why do these incidents occur?
Ransomware attacks have traditionally employed diverse methods, such as phishing, credential theft, vulnerability exploitation, and more.
Social engineering, or more specifically in this case, vishing (voice phishing) has become more effective in recent years for a number of reasons:
- Advanced Spoofing Techniques: Attackers have become adept at spoofing phone numbers to make it appear as though their calls are coming from legitimate sources. This can deceive individuals into answering calls they might otherwise ignore.
- Social Engineering: Vishing attacks often involve convincing social engineering tactics. Attackers gather personal information from various sources—in this case, the LinkedIn profile of a senior MGM staff member—to make their calls more convincing.
- Ease of Execution: Vishing attacks can be executed with relatively low technical skills and resources. This accessibility means that a broader range of threat actors can engage in such attacks.
- Remote Work: The rise of remote work has led to more reliance on phone and video calls for communication. Attackers have seized this opportunity to exploit the changing communication landscape.
Targeting IAM platforms is a well-known tactic employed by threat actors, providing them with persistent access to organizations and expanding their privileges across systems, resulting in increased harm. This strategy is far from novel, but one that yields tremendous value for attackers seeking strong access footholds.
Once the threat actors were discovered and noticed, MGM’s Okta sync servers were terminated, and the ransomware phase of the attack was underway, thanks to the BlackCat/ALPHV ransomware group. Ransomware-as-a-Service (RaaS) is a thriving industry within the criminal supply chain. Similar to how legitimate businesses depend on SaaS applications, criminal groups like BlackCat/ALPHV offer professional services that complement the original attacker’s capabilities, including malware development, command-and-control services, Tor leak sites, malware support, and even victim negotiation services.
Seeing Caesars Entertainment, the largest U.S. casino chain, pay approximately $15 million in ransom after a severe breach, cybercriminal groups would find ample motivation to explore the opportunities before them.
What can be done?
The obvious element of security training and vigilance absolutely should not be discounted, as the attacker’s crafty operationalization of social media (LinkedIn) victim data helped them deceive the MGM IT Helpdesk operators to land that all-important initial access vector.
Minimizing exposure and attack surfaces is paramount when facing threats like these, combining social engineering and vishing, credential harvesting, cloud account hijacking, and ultimately ransomware. Here are some tips that can help deflect sophisticated threats such as these:
- Reduce the Blast Radius: Segregate internal system assets, whether on premises or in the cloud. Even in cases where threat actors impersonate and successfully trick their way into corporate environments, if you’ve isolated and segmented your resources using Zero Trust principles, you’re drastically restricting their movements and minimizing the attack surface.
- Halt Compromised Users and Insider Threats: Utilize inline application and data inspection, in addition to extensive behavioral analytics to identify and stop potential attackers—whether external threats or insiders with malicious intent.
- Minimize External Attack Surface: Directly link users and access requests to applications and services to restrict lateral movement. In the case of MGM’s attack, moving laterally between Okta, Microsoft Azure, and finally the on premise ESXi servers made the hack possible.
- Prevent Data Loss: Deploy inline data loss prevention across all potential threat vectors and leakage channels. In the unfortunate event of an intruder gaining unauthorized access, if their actions on your data are prevented, you can dramatically reduce the impacts of breaches.
- Conduct Frequent Audits and Assessments: Regular cybersecurity audits assess compliance and reveal knowledge gaps, as well as highlight weaknesses and vulnerabilities that provide the all-important initial access vector for cybercriminals.
- Continually Educate Employees: Vishing is intensifying as a strong weapon in attackers’ arsenals. Many individuals are unaware of vishing as a threat vector, or their susceptibility to vishing attacks, leading them to let their guard down when responding to phone calls. This lack of awareness can make them vulnerable to manipulation.
References:
- https://www.mandiant.com/resources/blog/unc3944-sms-phishing-sim-swapping-ransomware
- https://www.bleepingcomputer.com/news/security/mgm-casinos-esxi-servers-allegedly-encrypted-in-ransomware-attack/
- https://techcrunch.com/2023/09/14/mgm-cyberattack-outage-scattered-spider/
- https://www.bleepingcomputer.com/news/security/caesars-entertainment-confirms-ransom-payment-customer-data-theft/
Use Skyhigh Security?
- Monitor user activity in Okta and review threats detected by User and Entity Behavior Analytics (UEBA) and machine learning algorithms.
- Detect internal and external threats to Microsoft Azure infrastructure, in addition to capturing all user activity to support forensic investigations.
- Adopt Zero Trust principles to enable tighter network security and segmentation of private apps and resources, such as Okta, Microsoft Azure, and VMware ESXi server infrastructures.
- Deny unauthorized data transfers and activities, even from internal applications via remote connections.
- Measure the risks a user might pose to your organization’s cloud services and data.
- Establish device posture profiles to be assessed against for connection requests.
- Continuously monitor activities for anomalies and violations.
With over 11 years’ worth of extensive cybersecurity industry experience, Rodman Ramezanian is an Enterprise Cloud Security Advisor, responsible for Technical Advisory, Enablement, Solution Design and Architecture at Skyhigh Security. In this role, Rodman primarily focuses on Australian Federal Government, Defense, and Enterprise organizations.
Rodman specializes in the areas of Adversarial Threat Intelligence, Cyber Crime, Data Protection, and Cloud Security. He is an Australian Signals Directorate (ASD)-endorsed IRAP Assessor – currently holding CISSP, CCSP, CISA, CDPSE, Microsoft Azure, and MITRE ATT&CK CTI certifications.
Candidly, Rodman has a strong passion for articulating complex matters in simple terms, helping the average person and new security professionals understand the what, why, and how of cybersecurity.
Attack Highlights
- The attackers gathered data via LinkedIn and targeted senior MGM personnel likely to have high privileges in their Okta infrastructure.
- They used this information to perform vishing (voice phishing) attacks by contacting MGM IT Helpdesk services, impersonating the privileged victim(s), and asking IT Helpdesk to reset the Multi-Factor Authentication requests of the victim user(s).
- Upon successfully vishing, the threat actors proceeded to compromise MGM’s Okta systems, gaining super administrator privileges to their Okta and Microsoft Azure environments.
- The perpetrators claimed to have exfiltrated an unspecified quantity of data from MGM’s network once inside.
In response to MGM’s incident response teams terminating Okta sync servers to flush out the attackers, attention was shifted to several hundred MGM owned ESXi servers that hosted thousands of VMs. These VMs supported hundreds of systems and thousands of devices widely used in their hospitality and gambling facilities. - This triggered a domino effect. As ESXi hosts were encrypted sequentially, applications crashed in a chain reaction. Hotel room keys became non-functional, dinner reservations were disrupted, point-of-sale systems couldn’t process payments, guests couldn’t check in or out, and slot machines were entirely inaccessible.









