Resources
INTELLIGENCE DIGEST
Hickory Dickory Dock: Privacy Issues Plague TikTok Globally
Is Your Data Dancing to a Different Beat?
By Rodman Ramezanian - Global Cloud Threat Lead
April 24, 2023 7 Minute Read
What started as a means of generating laughs through short video clips during the coronavirus pandemic, TikTok has taken the attention-capturing short-form video format and solidified its place among the most popular social media apps. But just like other foreign-owned apps that go viral, Chinese-owned TikTok continues to face scrutiny over its data collection and privacy practices. This time, however, it’s not only the United States sounding the alarm bell.

Citing a threat to “sovereignty and integrity,” Australia joins a handful of global governments, including India, the United Kingdom, the United States, Canada, and many countries throughout Europe, calling for the TikTok app to be removed from all officials’ mobile phones. Governments are beginning to take TikTok risks more seriously, but, with over 1 billion monthly active users, are corporations and non-governmental organizations doing the same?
According to the Center for Internet Security, “The data TikTok collects from users contains sensitive information and is often taken without the user’s explicit knowledge.” This data includes, but is not limited to, “device brand and model, Operating System (OS) version, mobile carrier, browsing history, app and file names and types, keystroke patterns or rhythms, wireless connections, geolocation.” TikTok even goes as far as collecting other personally identifiable information (PII) such as age, image, personal contacts, and other data collected through its integrated single sign-on (SSO) capability.
Considering that the app can collect “the content of [messages] and information about when [messages are] sent, received and/or read,” and, particularly with the TikTok CEO’s recent Congressional hearing adding further substance to the overall dialogue, it’s easy to see why large organizations and corporate enterprises across the globe are increasingly wary of TikTok and are expressing concern about the protection of the personal and corporate data it collects.
Why do these breaches occur?
While social media has always posed various security risks, including vulnerability to phishing and fraud, a primary point of concern for governments, enterprises, and other large organizations alike is the blurring of lines between personal and corporate usage of the devices on which TikTok is installed and consumed.
Moreover, the potential for data misuse by both external and internal parties is a significant concern. This is due to how intertwined online platforms and services are, with shared authentication tokens, single sign-on integrations, data portability, and more. The ramifications of potential data theft and misuse could be grave, especially given the widespread use of web and cloud services.
The question is how many organizations care about security threats enough to support a TikTok ban versus how many are entirely unaware of the risks they’re taking.
As with any web, cloud, or mobile threat, it’s crucial for security teams to learn and understand the key risk factors. How does TikTok handle data? How does it identify and authenticate users and devices securely? What kind of traffic and content can be shared and consumed from it? Where are the service’s points of presence, and what does that mean for an organization’s risk appetite?
With today’s vast number of users, devices, locations, business requirements, and more, it’s sometimes difficult to take heavy-handed approaches by explicitly blocking access to certain services overnight. There is a lot to be said for educating users and introducing security guardrails in cases where an organization may not want to abruptly block services in one fell swoop.
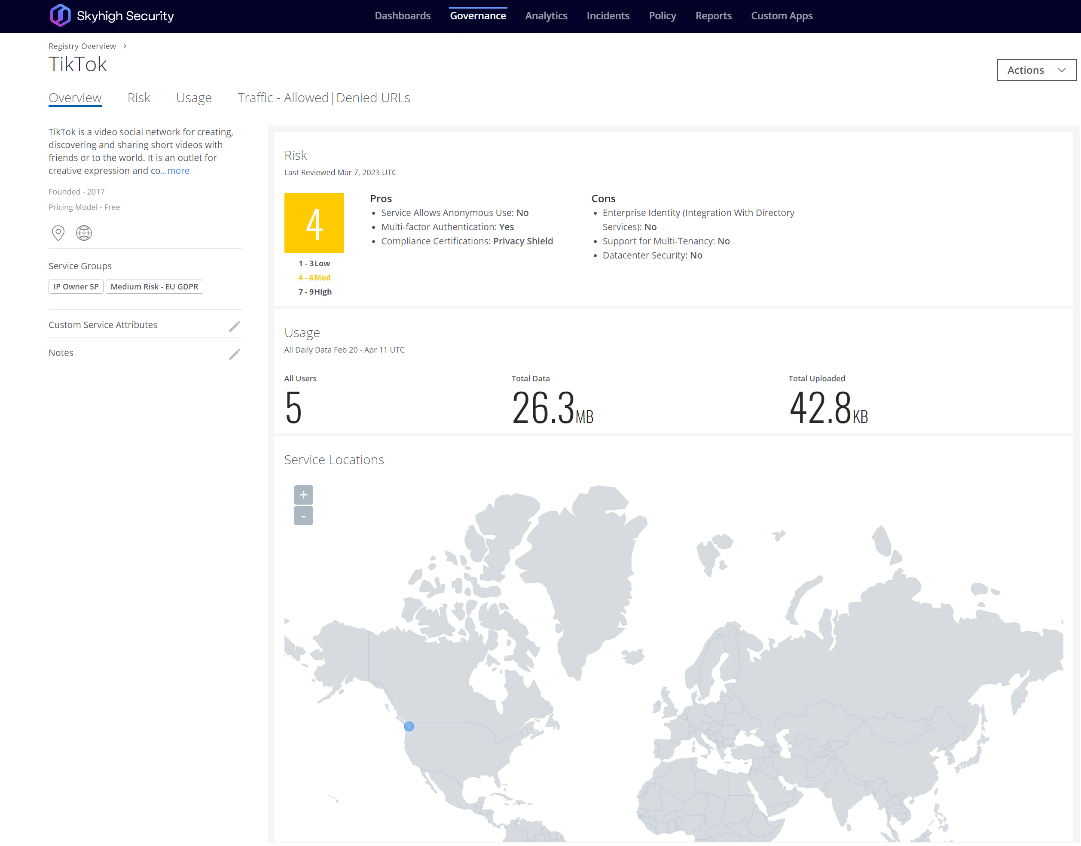
Skyhigh Security addresses this issue by detailing numerous risk attributes that need to be considered by security analysts as users navigate the turbulent waters surrounding TikTok as a platform and service. These include risk attributes pertaining to the data itself, the user/device, the service, the organization’s business practices, legal matters, and cybersecurity.
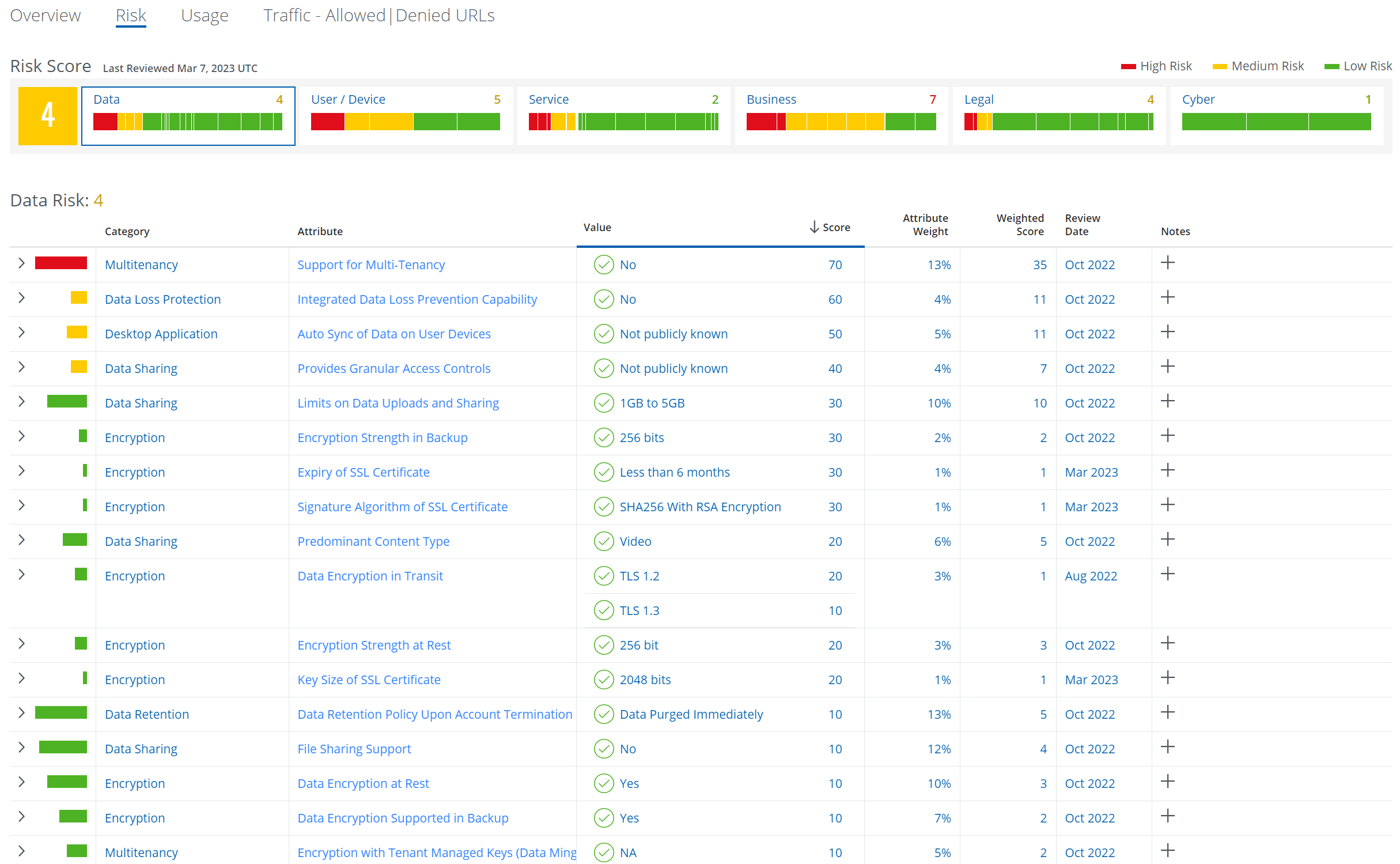
From there, security teams can begin to introduce data security controls, such as limiting/blocking of logins, uploads, and/or downloads; throttling of data bandwidth; introducing custom user education web pages; and other measures to not only curb data leakage from devices onto the TikTok platform, but, more holistically, to better control the flow of sensitive data from reaching users’ devices that may be consuming other questionable online services that may mishandle data.
What can be done?
Use Skyhigh Security?
- Use the Skyhigh Cloud Registry to leverage a proprietary and standardized risk algorithm.
- Leverage activity control rules to define criteria for acceptable user activities, such as login, upload, and/or download on managed devices.
- Implement shadow/web policies within locations where TikTok may be already banned and begin to limit and control access in others.
- Tailor your organization’s global risk weighting across numerous risk attribute categories.
- Create and assign service groups based on specific characteristics, such as data handling practices, global points of presence, recent breaches, and more.
With over 11 years’ worth of extensive cybersecurity industry experience, Rodman Ramezanian is an Enterprise Cloud Security Advisor, responsible for Technical Advisory, Enablement, Solution Design and Architecture at Skyhigh Security. In this role, Rodman primarily focuses on Australian Federal Government, Defense, and Enterprise organizations.
Rodman specializes in the areas of Adversarial Threat Intelligence, Cyber Crime, Data Protection, and Cloud Security. He is an Australian Signals Directorate (ASD)-endorsed IRAP Assessor – currently holding CISSP, CCSP, CISA, CDPSE, Microsoft Azure, and MITRE ATT&CK CTI certifications.
Candidly, Rodman has a strong passion for articulating complex matters in simple terms, helping the average person and new security professionals understand the what, why, and how of cybersecurity.
Attack Highlights
- Social media apps are entrenched in data and the devices they sit on—the same devices that are used for both personal and corporate purposes nowadays.
- TikTok, like all apps, potentially opens access to a user’s entire mobile phone. Mobile phone applications can offer credible potential for that app to bridge access to other things on the device—in this case, the data it holds.
- TikTok can also access and collect information from any other login sources or those that are linked to a user’s profile. This can include personal and/or corporate Google, Facebook, Twitter, or any other service used to authenticate users to TikTok.
- With the continued proliferation of bring your own device (BYOD) practices, the virtual line between personal and corporate usage is blurred. The same worrisome applications continue to coexist with vast amounts of corporate data points that seemingly end up in the wrong hands.
- Now with global governments acting to ban TikTok on government workers’ devices, businesses and other organizations are also being encouraged to rethink how they use TikTok as a platform and service.









