Resources
INTELLIGENCE DIGEST
Always Connected, Always Vulnerable: The Downside of Legacy VPN and Firewalls
Palo Alto Network’s recent vulnerability exposes organizations to lateral threat movement and data breaches
By Rodman Ramezanian - Enterprise Cloud Security Advisor
April 29, 2024 7 Minute Read
The past year has been a constant game of whack-a-mole with VPN vulnerabilities, leaving organizations that use outdated remote access systems wide open to potential cyberattacks. Hackers are exploiting critical flaws in everyday software, from VPNs—like the high-severity Ivanti CVEs and the Fortinet FortiVPN events—to firewalls like Palo Alto Networks PAN-OS and messaging applications like Telegram. By allowing adversaries to take complete control of devices through remote code execution or block access to devices with Denial-of-Service (DoS) attacks, these vulnerabilities put your valuable data at risk.
In December 2023, Chinese state-backed hackers exploited zero-day vulnerabilities (CVE-2023-46805 & CVE-2023-21887) in Ivanti VPN products, enabling unauthorized access through authentication bypass and remote control through remote command injection. Even after patches were released, attackers found new vulnerabilities (CVE-2024-21888) to bypass the fixes and continue their malicious activities.
This February, the U.S. Cybersecurity and Infrastructure Security Agency (CISA) sounded the alarm about another VPN attack. This time, the target was Cisco ASA security appliances, which combine firewall, antivirus, intrusion prevention, and virtual VPN capabilities. The culprit was a known vulnerability (CVE-2020-3259) exploited by the Akira ransomware group, which attacks both Windows and Linux systems. The cybercrime organization took advantage of misconfigured WebVPN/AnyConnect setups to steal data.
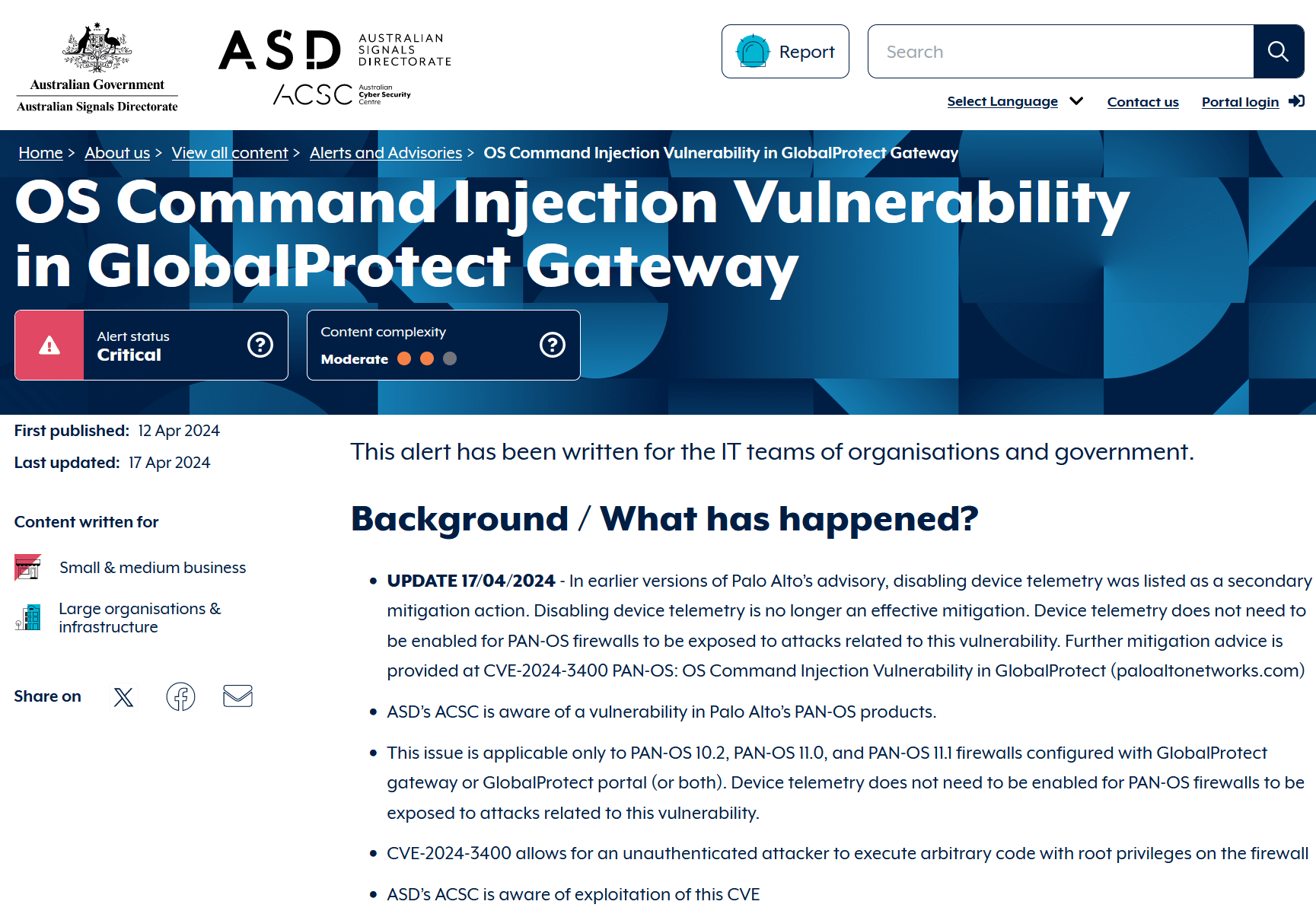
This most recent vulnerability is from Palo Alto Networks. This critical zero-day, tracked as CVE-2024-3400, impacts the vendor’s its GlobalProtect VPN product. The critical security hole found in Palo Alto Networks PAN-OS allows attackers to gain full control with root privileges of the firewall itself and the VPN connectivity it facilitates, all without requiring a username and password. To put it simply, this zero-day threat has the highest severity score possible: 10 out of 10.
In the initial discovery article released by Volexity, the research found that the attacker focused on exporting configuration data from the devices and then leveraging it as an entry point to move laterally within the targeted organizations.
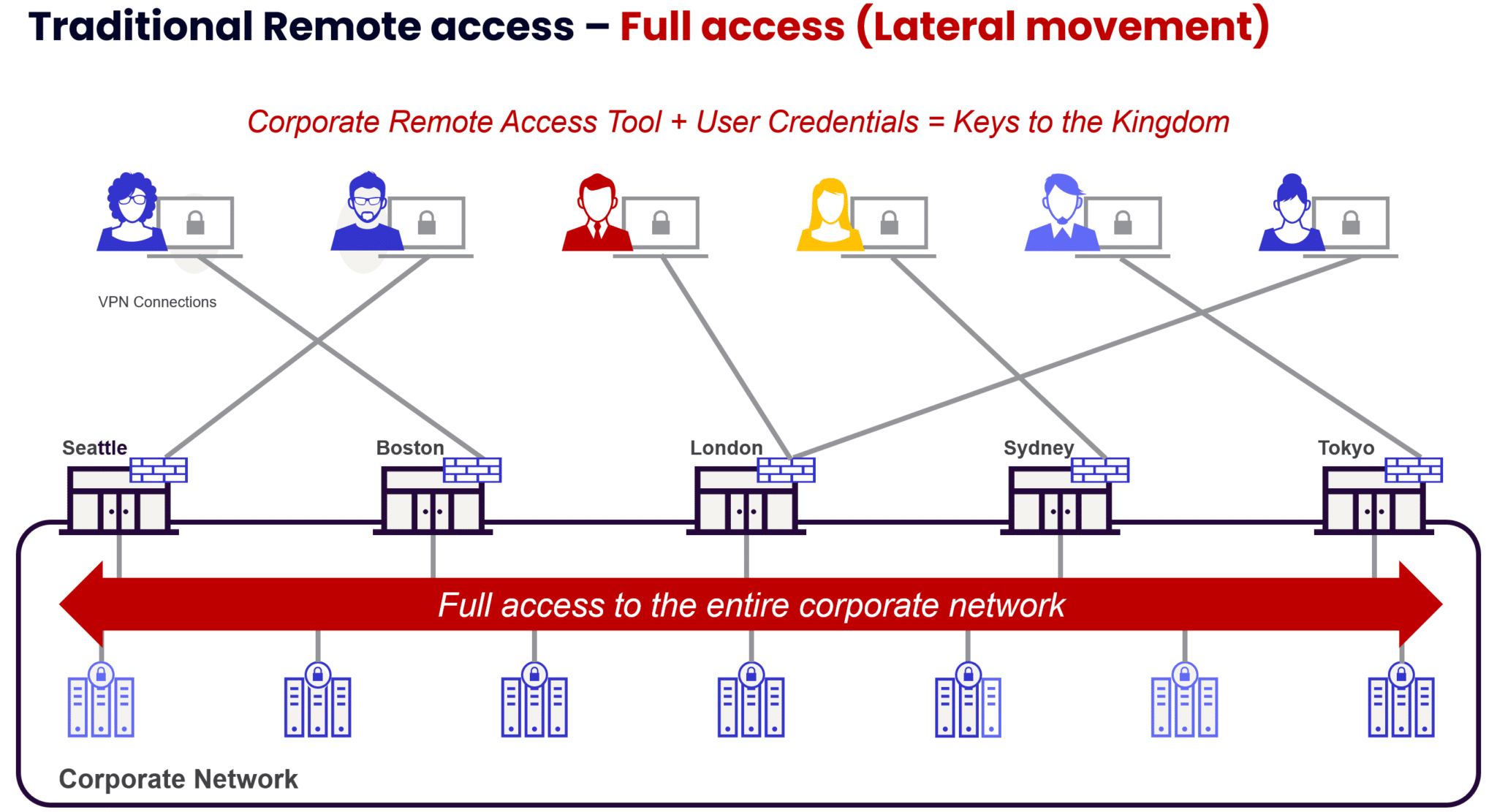
These repeated attacks using zero-day exploits highlight a concerning trend: the problem lies with the outdated architecture of VPNs themselves, not with any particular vendor.
Why do these incidents occur?
Over the past several years, SSL VPN products have been targeted by a wide range of threat actors, both financially motivated cyber criminals and nation-state hacktivists. How do you explain this phenomenon? The answer is a relatively simple one: SSL VPNs can serve as an entry point for accessing a treasure trove of valuable corporate data. They provide a direct path into a company’s network, making them a valuable staging ground for further attacks.
The surge in remote work after the COVID-19 pandemic has transformed SSL VPNs into a double-edged sword. Because they are easy to access, attackers can exploit remote workers’ susceptibility to phishing and other socially engineered attacks.
Recent VPN and firewall vulnerabilities, like the Palo Alto Networks GlobalProtect flaw, highlight another concerning trend. This isn’t about pointing the finger at specific vendors. Rather, it’s about the fundamental design flaw in these technologies. Organizations need to be aware that internet-facing assets like firewalls and VPNs are prime targets for breaches. Once attackers gain access, traditional legacy architectures allows them to move freely within the network, stealing sensitive data and compromising critical applications.
The US Cybersecurity and Infrastructure Security Agency (CISA) and the Australian Cyber Security Centre (ACSC) have published guidance recommending that organizations of all sizes—particularly those in government—act swiftly due to the severity of the vulnerability. These articles include additional resources to assist with patching and limiting exposure where possible.
Patching vulnerabilities remains crucial, but for a truly proactive defense against zero-day attacks, a Zero Trust architecture offers the most significant advantage.
There are a number of fundamental steps to help limit exposure:
- Minimize attack points: Make critical applications and vulnerable VPNs invisible online to prevent initial breaches.
- Confine breaches: Connect users directly to applications to minimize damage from compromised systems.
- Stop threats at the gate: Continuously inspect all traffic to automatically block emerging threats.
- Limit access privileges: Give users only the access they need in order to prevent unauthorized actions.
“Zero Trust” has become a buzzword in the security space, but, when done right, it’s an approach that has real value. By implementing Zero Trust principles and its underlying architecture, companies can effectively address the security risks plaguing traditional networks, including serious exposures from vulnerabilities in firewall and VPN products.
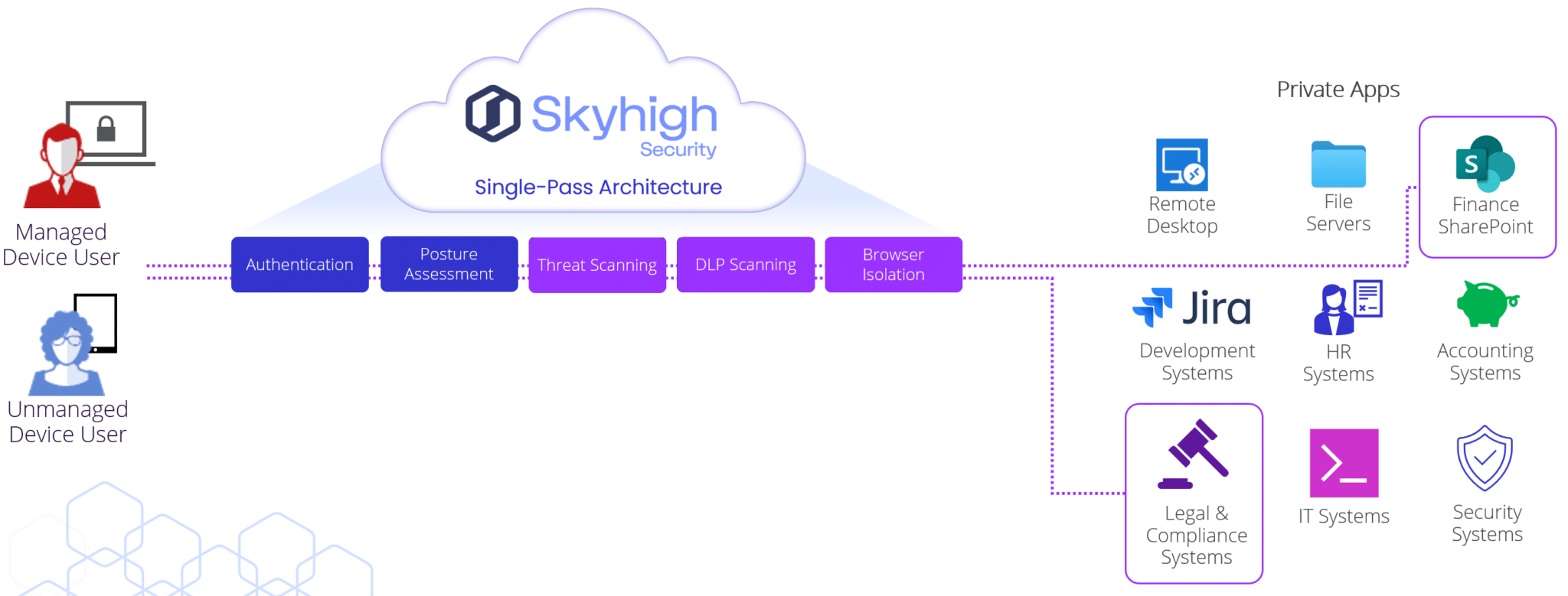
If you can minimize reliance on VPN and thereby nullify the risk of being exposed again by another vulnerability, why not explore that option? Zero Trust throws out the old rulebook. Unlike traditional networks secured by firewalls and VPNs, Zero Trust does not rely on a central “trusted zone.” Instead, it creates secure connections directly between users and the specific resources they need. This goes beyond just users and applications. Zero Trust can connect workloads, branch offices, remote workers, even industrial control systems.
Skyhigh Security enables this by facilitating a secure connection to authorized applications rather than directing the requesting user or device to the corporate network. Every user, device, and connection is continuously verified before access is granted to sensitive resources. Trust is never granted by default, ensuring data safety and integrity at all times, without compromising availability or performance for your users.
It’s time for security leaders to embrace Zero Trust. This cloud-based approach shrinks the attack surface by eliminating vulnerabilities associated with firewalls, VPNs, and other legacy technologies. By denying attackers their usual entry points, Zero Trust creates a stronger defense and more robust security posture.
References:
- https://www.cisa.gov/news-events/alerts/2024/04/12/palo-alto-networks-releases-guidance-vulnerability-pan-os-cve-2024-3400
- https://www.cyber.gov.au/about-us/view-all-content/alerts-and-advisories/os-command-injection-vulnerability-in-globalprotect-gateway
- https://security.paloaltonetworks.com/CVE-2024-3400
- https://therecord.media/vpn-zero-day-palo-alto-networks
Why Use Skyhigh Security?
- Adopt Zero Trust principles to enable tighter network security and segmentation of private applications and resources.
- Define device profiles and posture assessments for managed and unmanaged devices that request access to corporate resources, either internally or externally.
- Enable configuration audits to discover and monitor services exposed to unrestricted access.
- Evaluate user activities beyond initial logins to include user movements, behaviors, access to corporate services, locations, and many other potential anomalies.
- Block unmanaged devices, enforce Multi-Factor Authentication and many other contextual access policies to help stop the successful reuse of stolen cloud application credentials.
- Align threats, anomalies, and incidents to the MITRE ATT&CK framework to guide SOC analysts for investigations.
With over 11 years’ worth of extensive cybersecurity industry experience, Rodman Ramezanian is an Enterprise Cloud Security Advisor, responsible for Technical Advisory, Enablement, Solution Design and Architecture at Skyhigh Security. In this role, Rodman primarily focuses on Australian Federal Government, Defense, and Enterprise organizations.
Rodman specializes in the areas of Adversarial Threat Intelligence, Cyber Crime, Data Protection, and Cloud Security. He is an Australian Signals Directorate (ASD)-endorsed IRAP Assessor – currently holding CISSP, CCSP, CISA, CDPSE, Microsoft Azure, and MITRE ATT&CK CTI certifications.
Candidly, Rodman has a strong passion for articulating complex matters in simple terms, helping the average person and new security professionals understand the what, why, and how of cybersecurity.
Attack Highlights
- A critical vulnerability with the highest possible CVSS score of 10 out of 10 has been found in Palo Alto Networks PAN-OS, which is used to operate its firewall and VPN features.
- This vulnerability allows a remote, unauthenticated attacker to gain root privileges on the product and take full control of it. According to Palo Alto Networks, this vulnerability is actively being exploited in the wild at present.
- Attackers are using Palo Alto Networks firewalls as an entry point to move laterally within targeted organizations.
- Industry research and intelligence has found thousands of instances where the vulnerability in these products exposes organizations to the zero-day threats around the world.
- In one instance discovered by industry researchers, an attacker leveraged a compromised highly privileged service account on the Palo Alto Networks firewall to gain access to the internal network through the server message block (SMB) protocol.









