Resources
INTELLIGENCE DIGEST
Microsoft Azure environments hit by MERCURY attacks
Destructive Advanced Persistent Threat (APT) group pivots to cloud environments
By Rodman Ramezanian - Global Cloud Threat Lead
May 25, 2023 7 Minute Read
According to recent industry research, multiple campaigns and tools being executed by the MERCURY APT group (aka MuddyWater, Static Kitten) – widely considered to be affiliated with Iranian Ministry of Intelligence and Security (MOIS) interests – have been observed launching damaging attacks in Microsoft Azure cloud environments.
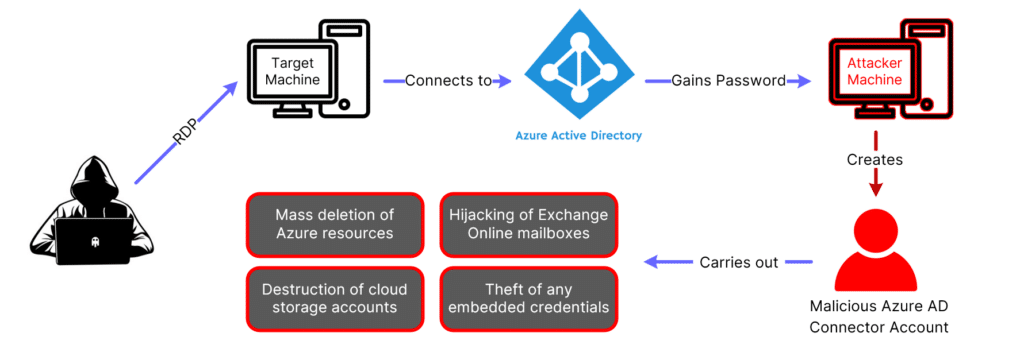
Research conducted by Microsoft shows how nation-state attackers have gained access to vulnerable, insecure on-site resources as well as cloud environments, enabling them to inflict extensive damage to the target’s infrastructure. Targeted organizations running hybrid Windows domain environments that combine local Active Directory (AD) and Azure Active Directory (AAD) have had their Azure Active Directory Connect agent manipulated, thereby gaining entry into their online Azure infrastructure, and subsequently destroying the victim’s Azure environment.
This ranged from wiping out their Azure virtual machine instances, server farms and workloads, virtual networks, storage accounts, and more.
Throughout their operations, the threat actors have actively targeted both on-premise and cloud environments. From what is currently known of this campaign, their primary objectives have been disruption and destruction.
Interestingly, this disruptive and destructive behavior is in line with commonly seen Iranian nation state attackers’ Tactics, Techniques, and Procedures (TTP), with specific reference to the damaging 2012 Saudi Aramco attacks at the hands of Iranian hackers, as well as their continued use of DDoS attacks and Wiper malware strains to overwrite systems or otherwise leave them unusable or unrecoverable (unless organizations have working backups).
Doubly interesting is the APT group’s strong pivot towards the Microsoft cloud ecosystem, with their past attacks focusing mostly on vulnerable, on-premises Exchange services and Fortinet security appliances, or more recently with online services such as Dropbox and OneHub.
Why do these incidents occur?
It should come as no surprise that today’s sophisticated hackers are increasingly focusing on cloud environments to further their agendas. Irrespective of geopolitics playing a part in this nation-state actor’s story, we continue to see exploitation of remote access tools as a prime initial access vector into target environments.
As most organizations continue their evolution into the cloud, hybrid infrastructures provide flexibility for requirements that cannot be fulfilled in cloud-only ecosystems, or may not yet be ready to be cloudified. Maintaining on-premise and cloud-native resources (presumably in a synchronized, hybrid fashion) enables these enterprises to enjoy the best of both worlds until more efficient methods can mature for them.
With this philosophy becoming more commonplace, threat actors relish the thought of flexing their muscles on the more traditional and established access vectors (say, remote desktop connection), to then ultimately be rewarded with a pivot-point into the target’s cloud infrastructure. Subsequently, that whole new cloud domain represents vast opportunity for theft, financial gain through ransom, disruption, or even just outright destruction as we see here.
What can be done?
Threats like these feast on vulnerable or exposed services that offer a beachhead into a target’s environment. From that point, it just becomes a matter of where and how malicious actors exploit excess privileges and permissions to carry out their attacks. Reducing your overall attack surface, at the very least, will go a long way towards thwarting the “low hanging fruit” temptations laid in front of threat actors. This means disabling or, at minimum, segmenting remote access services, private applications, or protocols that are no longer needed or shouldn’t be publicly accessible behind dated perimeter tools. Capabilities like Zero Trust Network Access (ZTNA) allow organizations to create software-defined perimeters and divide the corporate network into multiple micro-segments, preventing lateral movement of threats and reducing the attack surface in case of a breach.
Continuous access assessments and validations are also very effective mitigation techniques, since attempts of abuse can be identified and prevented on an individual case-by-case basis for each access request. On assessment of user identity, device identity, posture, and other contextual factors, ZTNA allows “least privilege” access to specific applications, and not the entire underlying network to any user with a successful login.
Since we’re also seeing configurations within Microsoft Azure environments being tampered with to pave the way for destruction, as well as abuses of privileged Microsoft Azure admin accounts, capabilities like Posture Management can help to detect and prevent activities and changes deemed anomalous or against corporate standards.
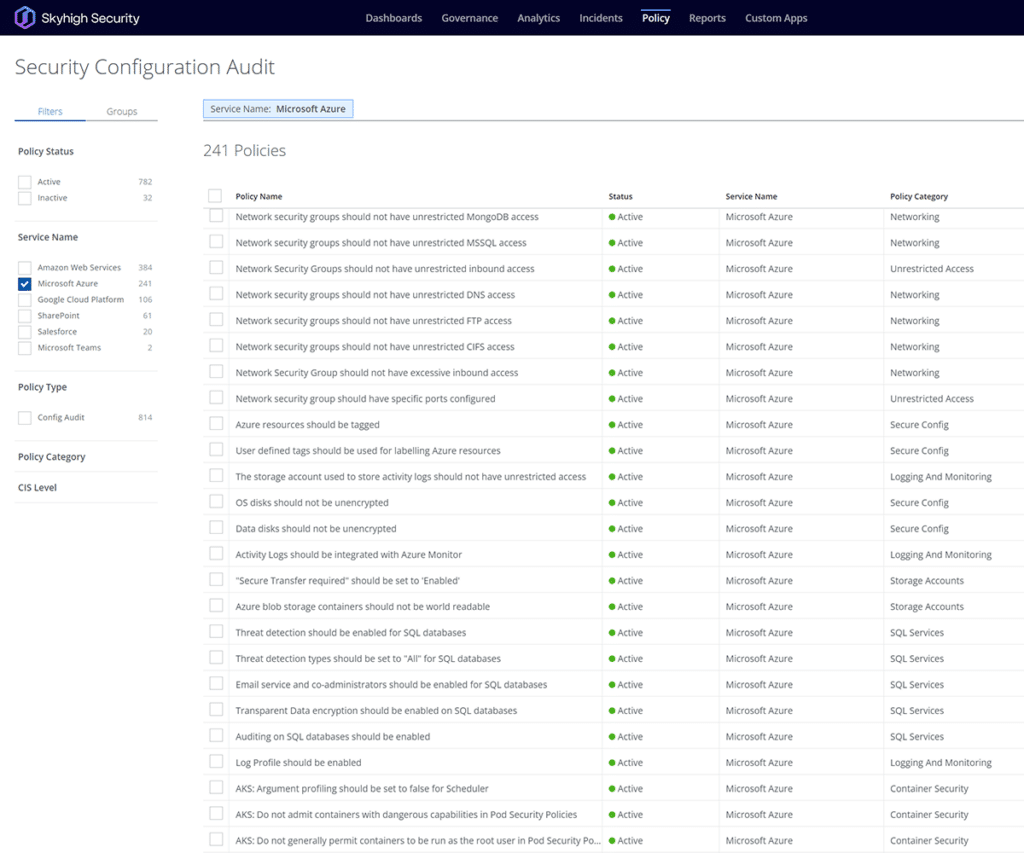
Skyhigh Security helps with this by extending Activity Monitoring and Security Configuration Audit features to Microsoft Azure infrastructures. To detect internal and external threats to Azure infrastructure, Skyhigh Security captures a complete record of all user activity in Microsoft Azure across multiple heuristics, detects threats, automatically takes risk-mitigating action, and supports forensic investigations. As threats are resolved, Skyhigh automatically incorporates this data into its behavioral models to improve detection accuracy.
Skyhigh dynamically and continuously updates thresholds for each user and group to identify activities indicative of insider threats. In-built Privileged User Analytics identify risk from inactive administrator accounts, excessive permissions, and unwarranted escalation of permissions and user provisioning.
Use Skyhigh Security?
- Enable Posture Management for Microsoft Azure environments to detect and prevent configuration changes.
- Leverage Private Access to enable tighter network security and segmentation of private apps and resources.
- Measure the risks a user might pose to your organization’s cloud services and data.
- Establish Device Posture Profiles to be assessed against for connection requests.
- Continuously monitor activities for anomalies and violations.
- Make use of policy templates for Microsoft Azure rated against Skyhigh, CIS Levels 1 & 2, PCI DSS, HIPAA, and NIST.
With over 11 years’ worth of extensive cybersecurity industry experience, Rodman Ramezanian is an Enterprise Cloud Security Advisor, responsible for Technical Advisory, Enablement, Solution Design and Architecture at Skyhigh Security. In this role, Rodman primarily focuses on Australian Federal Government, Defense, and Enterprise organizations.
Rodman specializes in the areas of Adversarial Threat Intelligence, Cyber Crime, Data Protection, and Cloud Security. He is an Australian Signals Directorate (ASD)-endorsed IRAP Assessor – currently holding CISSP, CCSP, CISA, CDPSE, Microsoft Azure, and MITRE ATT&CK CTI certifications.
Candidly, Rodman has a strong passion for articulating complex matters in simple terms, helping the average person and new security professionals understand the what, why, and how of cybersecurity.
Attack Highlights
- MERCURY threat actors exploit vulnerable, unpatched internet-facing devices and web applications to initially access the victims’ environments.
- Following successful exploitation, the operators deploy web shells on those assets to allow them to execute system commands remotely.
- Local user accounts are created to enable escalation of privileges into Administrator mode, with the goal being to eventually reach the target Domain Controllers for further propagation.
- If the targeted organization is running hybrid Windows domain environments combining local AD and Azure AD services, the threat actors exploit any privileged accounts created by the Azure AD Connect agent. This agent serves as the “bridge” between local AD and Azure AD environments to keep them in sync, with additional features such as password synchronization for shared identities, object syncing, and more.
- Once the attackers successfully sign into the Microsoft Azure environment – via the compromised account – account permission sets and role privileges are tampered with to stage further action.
- Destruction of Microsoft Azure assets begins, including deletion of workloads, VM images, servers, disks, storage accounts, and various other service instances in the Azure account.