Resources
INTELLIGENCE DIGEST
Another Sizeable Cloud Storage Repository Falls Victim To Ransom Attack
Fortinet’s cloud-hosted data store infiltrated by unauthorized access.
By Rodman Ramezanian - Enterprise Cloud Security Advisor
September 30, 2024 7 Minute Read
Cloud storage repositories have become an increasingly lucrative target for cybercriminals, offering a veritable buffet of sensitive data ripe for exploitation. No organization is immune to these threats, regardless of industry, size, experience, or financial resources. From small startups to multinational corporations, educational institutions to government agencies, all face the risk of their cloud-stored data falling into malicious hands.
The shift towards cloud storage has inadvertently simplified the attack vector for many hackers. Rather than navigating complex layers of traditional network defenses to access on-premises databases, threat actors now focus on compromising cloud storage services. These platforms are often more accessible and can be breached using reused or stolen credentials. This method of attack is particularly effective due to the prevalence of password reuse across multiple services. As a result, a single compromised account can potentially grant access to a treasure trove of sensitive information stored in the cloud, making these repositories an attractive and efficient target for cybercriminals seeking to maximize their impact with minimal effort.
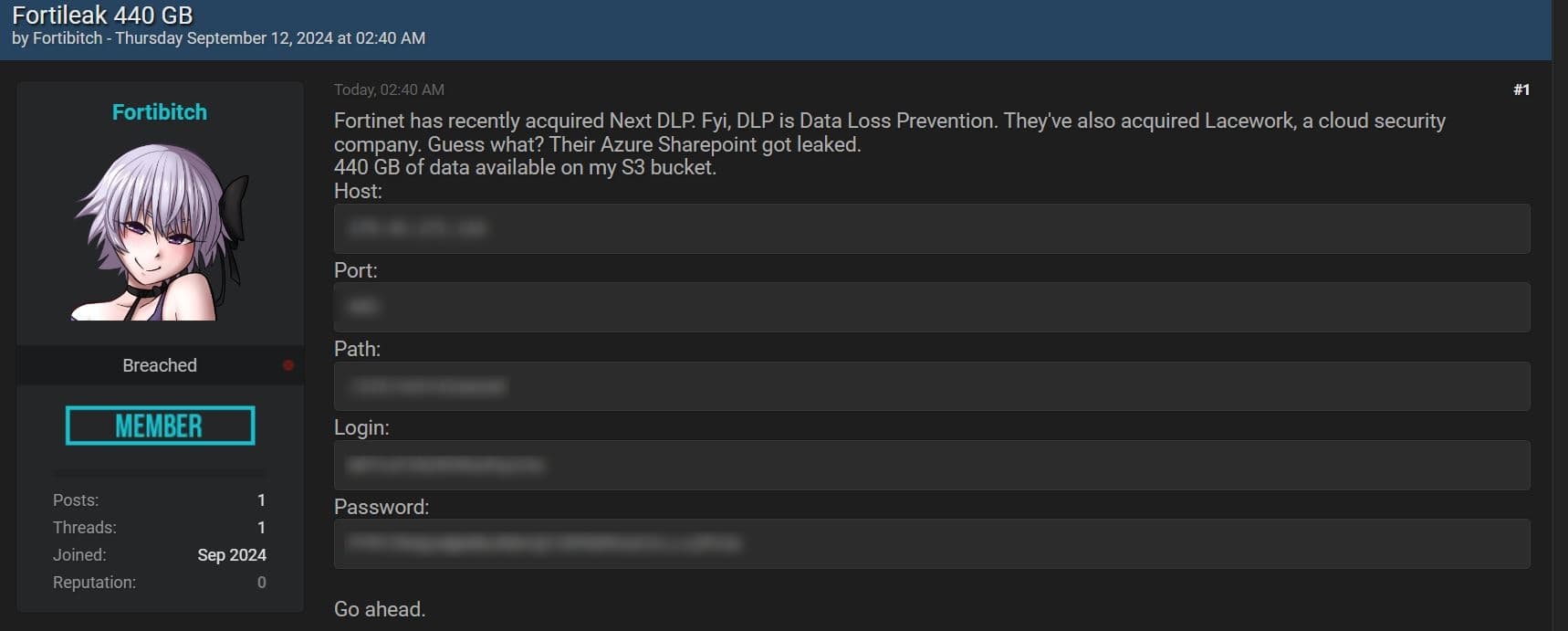
Cybersecurity firm Fortinet has confirmed a data breach that impacted some customer data. Earlier this month – September 12 to be exact – a group known by its provocative name ‘Fortibitch’ released a data cache, which is believed to have been stolen from Fortinet’s Microsoft Azure SharePoint server used to store customer data. Unfortunately, as these incidents tend to play out, the threat actors have now made the stolen data available for download on the dark web – contained within an Amazon S3 bucket – after Fortinet allegedly declined paying the ransom demands.
Why do these incidents occur?
Sadly, many organizations in recent times have found themselves in comparably unenviable situations. Whether it spawns from a resource misconfiguration, or the compromising of authorized credentials, the sheer breadth and size of cloud platforms – like Microsoft Azure in this case – present no shortage of opportunities for threat actors to try their hand at finding a way – any way – into an organization’s cloud-extension of their bases.
As Fortinet have confirmed in their own words: “An individual gained unauthorized access to a limited number of files stored on Fortinet’s instance of a third-party cloud-based shared file drive, which included limited data related to a small number of Fortinet customers”.
Now, the analysis of this incident is in no way intended to “kick anyone while they’re down” – but it does seek to highlight and reinforce some fundamental security principles that can mitigate or, at the very least, reduce the blast radius of similar attacks in the future.
Although Fortinet are yet to confirm in greater detail exactly how the unauthorized credentials were compromised and used to access the private Azure SharePoint server, judging by a myriad of similar attacks in the past, you’d probably be safe to presume that either social engineering, credential harvesting, and/or phishing techniques played a key role in obtaining these privileged credentials granting entry into Fortinet’s inner sanctum hosted on Azure.
This underscores the strong case for adopting Zero Trust principles, where the impact of compromised credentials would be minimal due to the segregation and limited privileges of any single account.
Let’s say: you have a limited number of privileged accounts that exclusively maintain access to a treasure trove of highly sensitive, cloud-hosted customer data. Now, in this scenario, it wouldn’t matter how targeted or susceptible the respective users (or their accounts) are by social-engineering threat actors or phishing opportunists. The reality would be that even if an attacker could compromise those account credentials, obtain a session token or authenticated cookie perhaps, or even manage to side-step Multi-Factor Authentication (MFA) mechanisms, the strongest and most powerful level of access they could hypothetically achieve would be extremely limited by principles of least privilege; a core tenet of the Zero Trust philosophy.
What can be done?
User credentials have become the crown jewels of digital security, demanding rigorous safeguarding measures. The 2024 Verizon Data Breach Report provides sobering insights, revealing that human error accounts for a staggering 68% of breaches, while misconfigurations and related issues contribute to one-third of security incidents. These statistics underscore the critical need for organizations to invest in advanced security measures that can establish and monitor normal patterns of user activity within their networks. By doing so, security teams can swiftly identify anomalous behavior and address potential threats before they escalate into full-scale breaches.
In today’s cybersecurity climate, the question is no longer if a breach will occur, but when. This reality is starkly illustrated by the numerous high-profile security incidents globally, all of which involved the compromise of sensitive data. It’s a non-negotiable for organizations to prioritize investment in data-aware security solutions.
Bringing it back to security fundamentals; Multi-Factor Authentication (MFA) remains a critical tool that should be implemented wherever possible. The recent Fortinet breach serves as yet another stark reminder of how static, valid credentials can be obtained and exploited to gain deeper access into a victim’s infrastructure – whether it’s traditional on-premises systems or cloud-based platforms like Azure SharePoint.
The Fortinet incident further emphasizes the importance of adopting a Zero Trust architecture. Despite the implementation of Single Sign-On (SSO) and other access management products, the continued reliance on static, privileged credentials – which remain prime targets for threat actors – essentially leaves the front door wide open to organizations’ assets. Zero Trust doesn’t rely on a single point of authentication. Instead, it continuously verifies the user’s identity throughout the session. Even if an attacker obtains valid credentials, they would face ongoing challenges to maintain access. And besides, even if credentials are unfortunately compromised, unauthorized users would only be granted the minimum permissions necessary for that role they’re exerting control over. This limits the potential blast radius and threat of lateral movements, too.
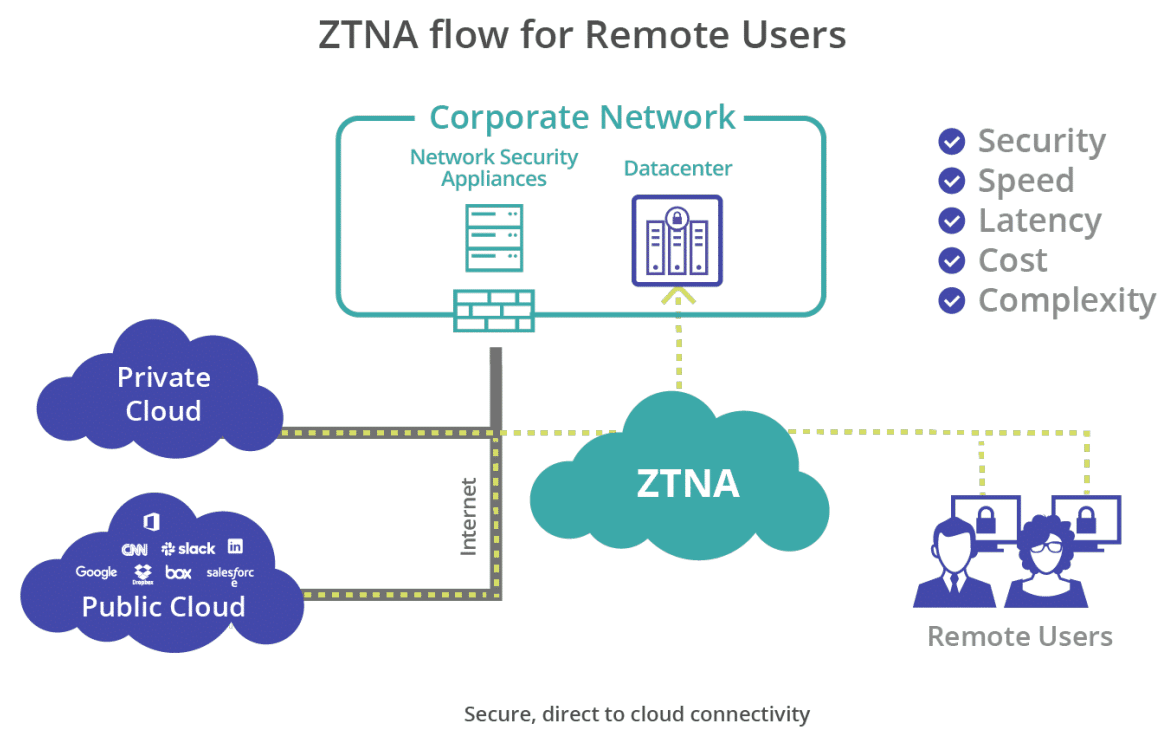
The typical modus operandi of cybercriminals and malicious insiders involves mimicking legitimate user behavior, starting with the login process. This is why Zero Trust architecture leverages continuous authentication and posture checks, monitoring the user’s (or requesting entity’s) context, status, and activities beyond the initial point of authentication.
However, authentication is just the beginning. Organizations must also ensure that data within their apps, services, or platforms is handled and transacted in ways that align with their security policies. This necessitates the convergence of data protections across web, cloud, and private applications (ZTNA). Solutions like Skyhigh Security offer deep data inspection and classification using inline Data Loss Prevention (DLP) to prevent inappropriate handling of sensitive data by remote users, regardless of their location or device.
So, if an unauthorized user posing as someone privileged suddenly extracts something like 440 GB of data out of the cloud platform, you’d want your Data Loss Prevention to undoubtedly detect and block that before it’s too late!
By unifying DLP and threat protection across common leakage channels – including devices, web, cloud, and private apps – security teams can benefit from end-to-end visibility and control over sensitive data. This holistic approach to data security is crucial in an era where data breaches can have devastating consequences for organizations of all sizes and industries.
References:
Use Skyhigh Security?
- Leverage Private Access policies to enforce principles of Zero Trust, controlling verified access directly into private applications, web, and cloud resources.
- Define Device Profiles and Posture Assessments for managed/unmanaged devices requesting access to corporate resources, either internally or externally.
- Enable configuration audits to discover misconfigurations before they’re exploited, and monitor services exposed to unrestricted access.
- Evaluate user activities beyond initial logins to include user movements, behaviours, access to corporate services, locations, and many other potential anomalies.
- Block unmanaged devices, enforce Multi-Factor Authentication and many other contextual access policies to help stop the successful reuse of stolen cloud application credentials.
With over 11 years’ worth of extensive cybersecurity industry experience, Rodman Ramezanian is an Enterprise Cloud Security Advisor, responsible for Technical Advisory, Enablement, Solution Design and Architecture at Skyhigh Security. In this role, Rodman primarily focuses on Australian Federal Government, Defense, and Enterprise organizations.
Rodman specializes in the areas of Adversarial Threat Intelligence, Cyber Crime, Data Protection, and Cloud Security. He is an Australian Signals Directorate (ASD)-endorsed IRAP Assessor – currently holding CISSP, CCSP, CISA, CDPSE, Microsoft Azure, and MITRE ATT&CK CTI certifications.
Candidly, Rodman has a strong passion for articulating complex matters in simple terms, helping the average person and new security professionals understand the what, why, and how of cybersecurity.
Attack Highlights
- On September 12, 2024, a threat actor emerged on the dark web marketplace BreachForums, claiming to have breached Fortinet’s Microsoft Azure SharePoint server and obtained up to 440 GB of data.
- The threat actor shared credentials to an S3 bucket supposedly containing the stolen data, stating that Fortinet refused to pay a ransom to stop its release.
- Fortinet later confirmed that “An individual gained unauthorized access to a limited number of files stored on Fortinet’s instance of a third-party cloud-based shared file drive, which included limited data related to a small number of Fortinet customers”
- According to Fortinet, the cloud storage repository in question held a small amount of data, affecting less than 0.3% of Fortinet’s customers. Following an investigation, the company found no evidence of any malicious activity impacting customers or any disruption to its operations, products, or services because of the incident.
- Further details surrounding exactly how the credentials and impacted account(s) were compromised are not yet known or reported by Fortinet at this time.









